Palo Alto Networks turned to high-speed security lack in its Pan-OS software, which could lead to bypass authentication.
Vulnerability tracked as Cve-2025-0108Carries CVSS 7.8 out of 10.0. However estimate is reduced to 5.1 if access to management interface is limited jump.
“Authentication software on Palo Alto Setworks Pan-OS networks allows unauthorized attackers with network access to the management web interface to get around authentication, otherwise requires Pan-OS web interface and causes certain scenarios”, “Palo Alto Networks” – Note In advisory.
“When referring to these PHP scenarios, the removed code does not allow, it can adversely affect Pan-OS integrity and privacy.”
Vulnerability affects the following versions –
- PAN-OS 11.2 <11.2.4-H4 (замацаваны ў> = 11.2.4-H4)
- PAN-OS 11.1 <11.1.6-H1 (замацаваны ў> = 11.1.6-H1)
- PAN-OS 11.0 (update to a supported fixed version when it reached the status of the end of November 17, 2024)
- PAN-OS 10.2 <10.2.13-H3 (замацаваны ў> = 10.2.13-H3
- PAN-OS 10.1 <10.1.14-H9 (замацаваны ў> = 10.1.14-H9)
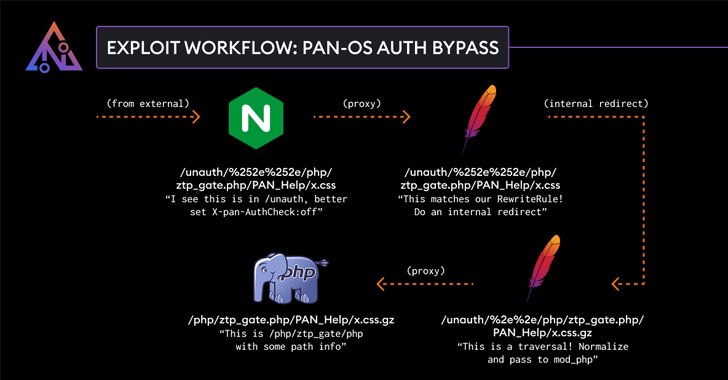
Researcher on Cyber/assets Adam Kese, who is credited with detecting and shortcoming report – Note The security defect is related to inconsistency in how Nginx and Apache interface components process incoming requests, leading to an attack on the catalog.
Palo Alto Networks also sent updates to solve the other drawbacks –
- Cve-2025-0109 (CVSS Assessment: 5.5) -Non -efficient Vulneration File Delete in Palo Alto SetWorks Pan -OS network interface, which allows the attacker to access the network to the management interface to delete specific files as a “no one”, including limited logs and files and files Configurations (fixed in Pan-OS Versions 11.4-H4, 11.1.6-H1, 10.2.13-H3 and 10.1.14-H9)
- Cve-2025-0110 (CVSS assessment: 7.3) -The distinction teams on Palo Alto setWorks Pan-OpenConfig, which allows the administrator authentication with the ability to make GNMI requests in Pan-OS web interface for management systems to bypass and launch. -Oos Openconfig plugin version 2.1.2)
To mitigate the risk that is vulnerably, it is highly recommended to disable access to interface interface from the Internet or on any unverified network. Customers who do not use OpenConfig can either choose to disable or remove the plugin from their instances.