In the past year, more than 140,000 phishing sites linked to a phishing-as-a-service (PhaaS) platform called Sniper Dz have been discovered, indicating that it is being used by a large number of cybercriminals to steal credentials.
“For would-be phishers, Sniper Dz offers an online admin panel with a directory of phishing pages,” Palo Alto Networks Unit 42 researchers Shehroz Faruqi, Howard Tong, and Alex Starov said in the technical report.
“Phishers can either host these phishing pages on infrastructure owned by Sniper Dz or download Sniper Dz phishing templates to host on their own servers.”
Perhaps even more profitable is the fact that these services are provided for free. However, credentials collected through phishing sites are also shared with PhaaS platform operators, a method Microsoft calls double theft.
PhaaS platforms have become an increasingly common way for novice threat actors to enter the world of cybercrime, allowing even those with little technical experience to carry out phishing attacks at scale.
Such phishing kits can be purchased from Telegramwith dedicated channels and groups serving every aspect of the attack chain, from hosting services to sending phishing messages.
Sniper Dz is no exception in that the threat actors operate a Telegram channel with over 7,170 subscribers as of October 1, 2024. The channel was created on May 25, 2020.
Interestingly, a day after the Unit 42 report went live, the people behind the channel turned on auto delete option to automatically delete all messages after a month. This probably indicates an attempt to hide traces of their activities, although the previous messages remain intact in the chat history.
The PhaaS platform is available on Clearnet and requires account registration to “get your fraud and hacking tools,” according to the website’s homepage.
Video loaded on Vimeo in January 2021 reveals that the service offers ready-to-use scam templates for various internet sites such as X, Facebook, Instagram, Skype, Yahoo, Netflix, Steam, Snapchat and PayPal in English, Arabic and French. To date, the video has received more than 67,000 views.
Hacker News too identified educational videos uploaded to YouTube that walk viewers through the various steps required to download templates from Sniper Dz and set up fake landing pages for PUBG and Free Fire on legitimate platforms like Google Blogger.
However, it is not clear if they are related to the developers of Sniper Dz or if they are just customers of the service.
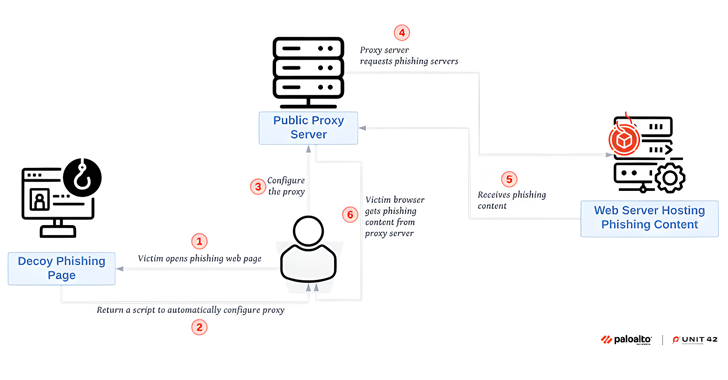
Sniper Dz has the ability to host phishing pages on its own infrastructure and provide special links to those pages. These sites are then hidden behind a legitimate proxy server (proxymesh(.)com) to prevent detection.
“The group behind Sniper Dz configures this proxy server to automatically download phishing content from its server without direct communication,” the researchers said.
“This technique can help Sniper Dz protect its backend servers, as the victim’s browser or security scanner will see that the proxy server is responsible for downloading the phishing payload.”
Another option for cybercriminals is to download phishing page templates offline as HTML files and host them on their own servers. In addition, Sniper Dz offers additional tools to convert phishing templates into Blogger format, which can then be hosted on Blogspot domains.
The stolen credentials are ultimately displayed in the admin panel, which can be accessed by logging into the Clearnet site. Unit 42 said it has seen a spike in phishing activity using Sniper Dz since July 2024, primarily targeting web users in the US.
“Sniper Dz phishing pages harvest the victim’s credentials and track them through a centralized infrastructure,” the researchers said. “This can help Sniper Dz collect victim credentials stolen by phishers using their PhaaS platform.”
The development comes after Cisco Talos discovered that attackers are abusing web pages connected to the SMTP backend infrastructure, such as account creation form pages and others that trigger a return email to the user, to bypass spam filters and distribute phishing emails .

These attacks take advantage of the poor input validation and sanitization common in these web forms to include malicious links and text. Other companies conduct credential attacks against the mail servers of legitimate organizations to gain access to email accounts and send spam.
“Many websites allow users to register for an account and log in to access certain features or content,” said Talos researcher Jason Schultz said. “Typically, after a user successfully registers, an email is sent to the user to confirm their account.”
“In this case, the spammers overloaded the name field with text and a link, which unfortunately is not checked or sanitized in any way. The email the victim received contains the spammer’s link.”
It also follows the discovery of a new email phishing campaign that uses a seemingly innocuous Microsoft Excel document to distribute a fileless variant Remcos RAT exploiting a known security flaw (CVE-2017-0199).
“Once the (Excel) file is opened, the OLE objects are used to trigger the download and execution of the malicious HTA application,” Trellix researcher Trishan Kalra said. “This HTA application then runs a chain of PowerShell commands that ends up injecting the fileless Remcos RAT into a legitimate Windows process.”