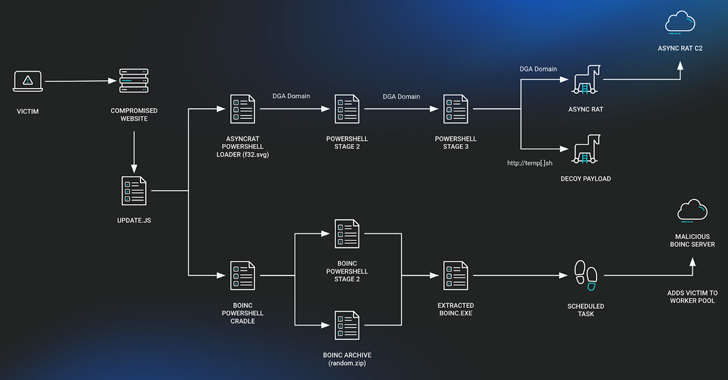
JavaScript downloader malware known as SocGholish (aka FakeUpdates) is used to deliver a remote access trojan named AsyncRAT as well as a legitimate open source project called BOINC.
BOINKshort for Berkeley Open Infrastructure Network Computing Client, is open source “volunteer computing”. platform is supported by the University of California to perform “large-scale, high-throughput distributed computing” using home computers running the program.
“In that way, it’s similar to a cryptocurrency miner (using computer resources to do work), and it’s actually designed to reward users with a specific type of cryptocurrency called Gridcoin designed for that purpose,” Huntress researchers Matt Anderson, Alden Schmidt, and Greg Linares said in a report released last week.

These malware are designed to connect to a domain controlled by an actor (“rosettahome(.)cn” or “rosettahome(.)top”), essentially acting as a command-and-control (C2) server to collect host data, deliver payloads and click further commands. As of July 15, 10,032 clients are connected to the two domains.
The cybersecurity firm said that while it did not observe any follow-up actions or tasks performed by the infected hosts, it speculated that “connections to the hosts may be sold as initial access vectors to be used by other actors and potentially used to execute a program – extortionists”.
SocGholish’s attack sequences typically begin when users land on compromised websites where they are prompted to download a fake browser update that, when executed, triggers the delivery of additional payloads to compromised machines.
The JavaScript loader in this case activates two separate threads: one causes the fileless AsyncRAT variant to be deployed, and the other causes BOINC to be installed.
The BOINC application, which is renamed to “SecurityHealthService.exe” or “trustedinstaller.exe” to avoid detection, sets the duration using a scheduled task using a PowerShell script.
The abuse of BOINC for malicious purposes did not go unnoticed by the project staff who currently under investigation problem and finding a way to “beat this malware”. Evidence of abuse goes back to at least June 26, 2024.
“The threat actor’s motivation and intent in uploading this software to infected nodes is unclear at this time,” the researchers said.
“Infected clients actively connecting to malicious BOINC servers pose a fairly high risk, as there is the potential for a motivated threat actor to abuse that connection and execute any number of malicious commands or software on the host to further elevate privileges or move parties across the network and compromise the entire domain.”
The development comes after Check Point said it is tracking the use of compiled V8 JavaScript by malware authors to bypass static detections and hide remote access trojans, stealers, bootloaders, cryptocurrency miners, cleaners and ransomware.
“In the ongoing battle between security experts and threat actors, malware developers continue to come up with new tricks to hide their attacks,” said security researcher Moshe Morelus. “It’s not surprising that they started using V8, as this technology is usually used to build software, as it is very common and very difficult to analyze.”