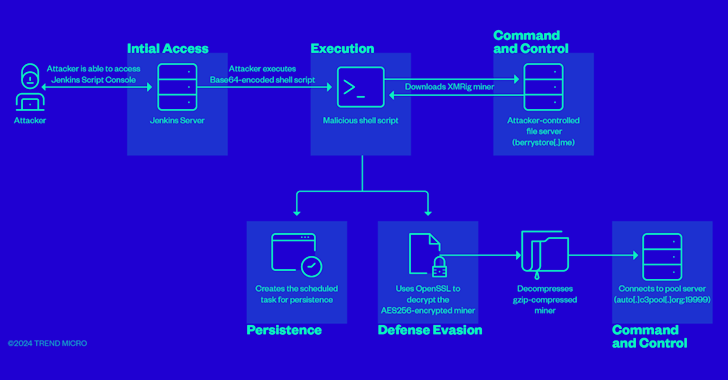
Cybersecurity researchers have discovered that attackers can use misconfigured instances of the Jenkins Script Console as a weapon for further criminal activity, such as cryptocurrency mining.
“Misconfigurations, such as misconfigured authentication mechanisms, open the ‘/script’ endpoint to attackers,” Shubam Singh and Sunil Bharti of Trend Micro said in a technical note published last week. “This could lead to Remote Code Execution (RCE) and abuse by attackers.”
Jenkins, the popular continuous integration and continuous delivery (CI/CD) has a Groovy scripting console that allows users to run arbitrary Groovy scripts in the Jenkins controller runtime.
The project maintainers explicitly state in the official documentation that the Groovy web shell can be used to read files containing sensitive data (such as “/etc/passwd”), decrypt credentials configured in Jenkins, and even reset security settings.
The console “offers no administrative controls to stop a user (or administrator) from influencing all parts of the Jenkins infrastructure if they are able to execute console scripts.” reads documentation. “Granting a regular Jenkins user access to the scripting console is essentially the same as granting them administrator rights in Jenkins.”
While access to the scripting console is usually restricted to authenticated users with administrative privileges, misconfigured Jenkins instances can inadvertently make the “/script” (or “/scriptText”) endpoint accessible over the Internet, making it ready for use by attackers who want to run dangerous teams.
Trend Micro said it has discovered cases where threat actors use a misconfiguration of the Jenkins Groovy plugin to execute a Base64-encoded string containing a malicious script designed to mine cryptocurrency on a compromised server by deploying a miner payload hosted on berrystore(. )me, and setting persistence.
“The script ensures that it has enough system resources to mine efficiently,” the researchers said. “To do this, the script checks for processes that consume more than 90% of CPU resources, and then terminates those processes. In addition, it terminates all terminated processes.’

To guard against such exploits, it is recommended to ensure proper configuration, implement strong authentication and authorization, perform regular audits, and limit Jenkins servers’ access to public access on the Internet.
The event comes as cryptocurrency theft through hacks and exploits spiked in the first half of 2024, allowing threat actors to steal $1.38 billion, up from $657 million for the year.
“The top five hacks and exploits accounted for 70% of the total stolen so far this year,” blockchain platform TRM Labs investigates. said. “Private key and seed phrase compromise remain the top attack vector in 2024, along with smart contract exploits and flash loan attacks.”