Financial institutions in Latin America are threatened by a banking Trojan called Mekotio (aka Melcoz).
That’s it findings from Trend Micro, which said it has recently seen a surge in cyberattacks spreading Windows malware.
Holeswhich is known to be in active use since 2015, is known to target Latin American countries such as Brazil, Chile, Mexico, Spain, Peru, and Portugal to steal banking credentials.
First documented by ESET in August 2020, this is part of a tetrad of banking Trojans focused on the region of Gildma, Javali and Grandoreirathe last of which was dismantled by law enforcement earlier this year.
“Mekotio has common characteristics for this type of malware, such as being written in Delphi, using fake pop-ups, backdooring and targeting Spanish- and Portuguese-speaking countries,” the Slovakian cybersecurity firm said at the time.
The malware operation struck in July 2021 when Spanish law enforcement 16 people were arrested belonging to a criminal network in connection with the organization of social engineering campaigns aimed at European users who delivered Grandoreiro and Mekotio.
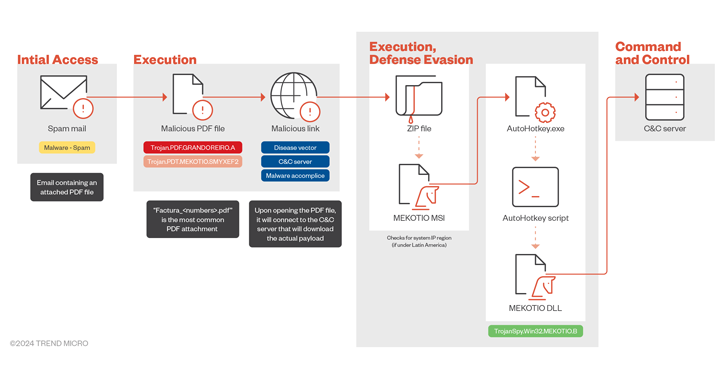
The attack chains involve the use of tax-themed phishing emails to trick recipients into opening malicious attachments or clicking on fake links that lead to the deployment of an MSI setup file, which in turn uses the AutoHotKey (AHK) script. to launch malware.
It should be noted that the infection process marks a slight deviation from the previous one previously detailed In November 2021, Check Point used an obfuscated batch script that runs a PowerShell script to download a second-stage ZIP file containing the AHK script.
Once installed, Mekotio collects system information and communicates with the control server (C2) to receive further instructions.
Its main purpose is to obtain banking credentials by displaying fake pop-ups that mimic legitimate banking sites. It can also take screenshots, record keystrokes, steal clipboard data, and set storage on the host via scheduled tasks.

The stolen information can then be used by threat actors to gain unauthorized access to users’ bank accounts and conduct fraudulent transactions.
“The Mekotio banking trojan is a persistent and evolving threat to financial systems, particularly in Latin American countries,” Trend Micro said. “It uses phishing emails to infiltrate systems to steal sensitive information while maintaining a strong foothold on compromised machines.”
The development comes after Mexican cybersecurity firm Scitum revealed details of a new Latin American banking trojan codenamed Red Mongoose Daemon, which, like Mekotio, uses MSI droppers distributed via phishing emails masquerading as invoices and tax invoices .
“Red Mongoose Daemon’s primary goal is to steal victims’ banking information through forgery PIX transactions through overlapping windows,” the company reports said. “This Trojan is intended for Brazilian end users and employees of organizations that have banking information.”
“Red Mongoose Daemon has capabilities to manipulate and create windows, execute commands, remotely control computers, manipulate web browsers, hijack clipboards, and mimic Bitcoin wallets by replacing copied wallets with wallets used by cybercriminals.”