A recently discovered critical security flaw affecting Progress Software MOVEit Transfer is already being observed attempts at exploitation in the wild shortly after details of the error were revealed publicly.
The vulnerability, noted as CVE-2024-5806 (CVSS score: 9.1), concerns an authentication bypass that affects the following versions:
- From 2023.0.0 to 2023.0.11
- From 2023.1.0 to 2023.1.6 and
- From 2024.0.0 to 2024.0.2
“An incorrect authentication vulnerability in Progress MOVEit Transfer (SFTP module) could allow authentication to be bypassed,” the company said in a statement. said in an advisory issued Tuesday.
There is also progress addressed another critical authentication bypass vulnerability related to SFTP (CVE-2024-5805, CVSS score: 9.1) affecting MOVEit Gateway version 2024.0.0.
Successful exploitation of the flaws could allow an attacker to bypass SFTP authentication and gain access to the MOVEit Transfer and Gateway systems.
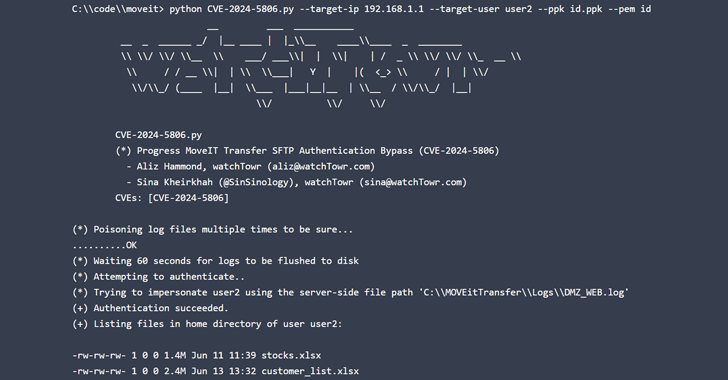
watchTowr Labs has since released more technical details about CVE-2024-5806, with security researchers Alise Hammond and Sina Heirkach noting that it could be a weapon to impersonate any user on the server.
The cybersecurity company went on to describe the flaw as two separate vulnerabilities, one in Progress MOVEit and one in the IPWorks SSH library.
“While the more disruptive vulnerability, the ability to impersonate arbitrary users, is unique to MOVEit, the less impactful (but still very real) forced authentication vulnerability will likely affect all applications that use the IPWorks SSH server “, – researchers. said.
Progress Software said the flaw in the third-party component “increases the risk of an underlying problem” if not fixed, urging customers to take the following two steps –
- Block public RDP inbound access to the MOVEit transfer server(s).
- Restrict outbound access to only known trusted endpoints from the MOVEit transfer server(s)
According to Rapid7, there is three prerequisites before exploit CVE-2024-5806: Attackers need to know an existing username, the target account can authenticate remotely, and the SFTP service is publicly available over the Internet.

As of June 25, data collected by Censys shows that there are about 2,700 instances of MOVEit Transfer online, most of them in the US, UK, Germany, Netherlands, Canada, Switzerland, Australia, France, Ireland and Denmark.
Another important issue in MOVEit Transfer widely abused in a series of Cl0p ransomware attacks last year (CVE-2023-34362CVSS score: 9.8), it is very important that users move quickly to upgrade to the latest versions.
The development comes after the US Cybersecurity and Infrastructure Security Agency (CISA) revealed that its Chemical Security Assessment Tool (CSAT) was targeted earlier this January by an unknown threat actor using security flaws in the Ivanti Connect Secure (ICS) appliance (CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893).
“This intrusion could have resulted in potential unauthorized access to top screen surveys, security vulnerability assessments, site security plans, personal security programs (PSPs), and CSAT user accounts,” the agency noted. saidadding that no evidence of data theft was found.
Update
In a statement released to The Hacker News, Progress Software said, “We have not received any reports that these vulnerabilities have been exploited, and we are not aware of any direct operational impact to customers.”
“We have already fixed the issue and are working to notify and advise affected customers of the impact,” Gent Heath, president and CEO of /n software, which supports IPWorks SSH, told the publication.
“The extent of the vulnerability depends on how developers use the component, and we expect it to be limited. It’s worth noting that the security researchers notified us just 24 hours before Monday’s release, when they’ve known and worked on it for weeks – which is unfortunate.”
/n software Provides information about CVE-2024-5806
The manufacturer IPWorks SSH has noted in the warning that bypassing authentication occurs only “after the developer has accepted the user’s credentials without validation.” It also says that as part of the library update, all unintended file and network access requests are prevented.
(The story has been updated after publication to emphasize that the attacks are exploitation attempts at this stage.)