Cybersecurity researchers pay attention to a number of cyber-fades aimed at financial organizations across Africa, at least July 2023, using the mix with open source and publicly available tools.
Palo Alto Networks Unit 42 tracks activity under Alias CL-CRIR-1014Where “CL” refers to “cluster” and “cri” means “criminal motivation”.
It is suspected that the ultimate goal of the attack is to gain initial access, and then sell it to other criminals in underground forums, making the actor threatening the initial broker (IAB).
“Actor threatens copy signature from legitimate applications to Learn the file signatureTo disguise your tools and mask your malicious events, “Researchers Tom Focteman and Guy Levy – Note. “Threatening actors often push legal products for malicious purposes.”
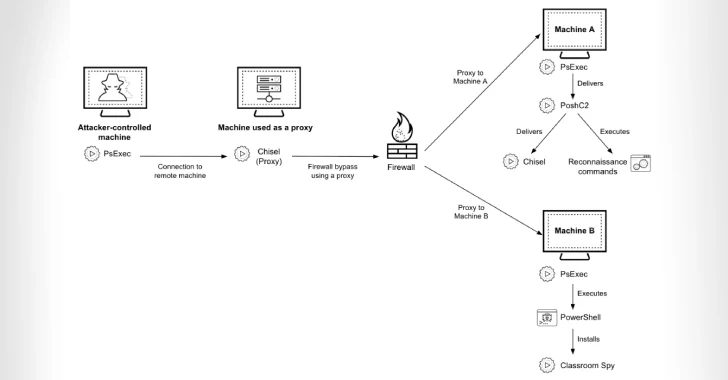
Attacks are characterized by deployment of such tools Poshc2 For commands and control (C2), Chisel for tunnel malicious network motion, and Spy in the classroom for remote introduction.
The exact method that the threatening subjects are used to violate target networks is unclear. Once the fixing is obtained, devastating chains were detected A Mo -Central Agent And later in the spy class control the machines and then throw a chisel to get around the firewalls and spread Poshc2 to other Windows hosts in a compromised network.
To identify the detection efforts, useful loads are transmitted as legal software using Microsoft, Palo Networks Cortex and Broadcom VMware Tools. POSHC2 is stored in systems using three different methods –
- Setting Services
- Saving the Fast Windows File File (LNK) in the tool in the starting folder
- Using a planned assignment called “Palo Alto Cortex Services”
In some incidents observed in cybersecurity, threats that stole users’ powers and used them to create proxies using POSHC2.
“POSHC2 can use proxy for communication with the team server and control (C2), and it seems that the actor threatened has adapted some POSHC2 implants specifically for the target environment,” the researchers said.
This is not the first time POSHC2 was used in attacks aimed at financial services in Africa. In September 2022 the check point minute The financial and insurance companies located on the ivory, Morocco, Cameroon, Senegala and Tag to deliver Metasploit, Poshc2, Dwservice and Asyncrat.
The disclosure of information occurs when Trustwave SpiderLabs shed light on a new ransom group called Dire Wolf, which has already stated 16 victims in the USA, Thailand, Taiwan, Australia, Bahrain, Canada, India, I, Peru and Singapore since its appearance last month. The best target sectors are technology, production and financial services.
Dire Wolf Locker analysis showed that it is written in the hunting and comes with the registration system, stop the hard list with 75 services and 59 applications, and interferes with recovery efforts by removing Shadow Copies.
“Although no initial access methods, exploration or lateral motion used by DIRE WOLF – Note.