Russian organizations are the goal of a phishing company that distributes malicious software called Purarat, according to the new Kaspersky findings.
“The company aimed at the Russian business began back in March 2023, but in the first third 2025, the number of attacks four times compared to the same period in 2024,” – a cybersecurity supplier – Note.
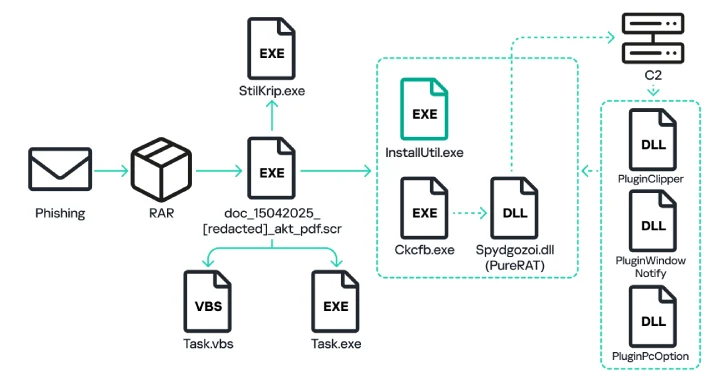
The attacks of attacks that have not been attributed to any specific actor threats begin with a phishing email that contains a RAR file or a link to the archive, which is masked as Microsoft Word or PDF -document using double extensions (“doc_054_ (edited) .pdf.Rar”).
The Archive File, which is present in the archive file, features a file, which upon startup, copies “%appdata%”.
Then the executed file continues to unpack another executed “ckcfb.exe”, launches “Anallutil.exe” system and introduces a decrypted module into it. “Ckcfb.exe”, from its part, withstands and transcripts the Dll “SpydGozoi.dll” file, which includes the main useful load of malware Purarat.
Purarat sets SSL-connections with the team server and control (C2) and transmits system information, including details about installed antivirus products, computer name and time that has passed since the system is launched. In response, the C2 server sends auxiliary modules to perform various malicious action –
- PluginPcoption, which is able to perform commands for self -resistance, restart executable file and closing or reboot computer
- Pluginwindownotify, which checks the name of the active window on keywords such as password, bank, WhatsApp, and perform appropriate subsequent actions such as unauthorized translations of the fund
- Connection that functions as Malicious software for Clipper Replacing the wallet for cryptocurrencies
“Trojan includes modules to download and launch arbitrary files that provide full access to the file system, registry, processes, cameras and microphone, implement the key function and give the attackers the ability to secretly manage the computer with the principle of the remote desktop,” Kosski said.
The original executable file that launches “ckcfb.exe” also retrieves the second binary, called “stilkrip.exe”, which is available on sale Purecrypter This was used to deliver various useful loads in the past. This is active since 2022.
“Stilkrip.exe” is designed to download “BGHWWHWMLR.WAV”, which follows from the above -mentioned attack
Purelogs – this The Non -Employment Theft of Information This can harvest data from web browsers, email clients, VPN services, messaging applications, browser extension, password managers, wallets applications and other programs such as Filezilla and Winscp.
“Purarat Backdoor and Purelogs Theft has extensive functionality that allows the attackers to gain unlimited access to infected systems and data of a confidential organization,” Kaspersky said. “The main vector of the attack on business was and remains e -mails with malicious investments or links.”