The Türkiye threat actor exploits the lack of security with zero day on the Indian communication platform called “Messenger withdrawal” as part of a cyber-spanning campaign since April 2024.
“These exploits have led to the collection of relevant users’ data for goals in Iraq,” Microsoft’s intelligence group – Note. “The targets of the attack are related to the Kurdish military personnel operating in Iraq, according to previously observed marble priorities aimed at dust.”
Activities has been associated with a group of threats it monitors as Marble dust (Previously silicon), which is also known as a space wolf, sea turtle, kurk –ko and unc1326. It is believed that the hacking of the crew was active, at least since 2017, although only two years later Cisco Talos recorded attacks aimed at public and private structures in the Middle East and North Africa.
Earlier last year, it was also defined as an orientation to telecommunications, media, Internet service providers (providers), information technology (IT), service providers and Kurdish sites in the Netherlands.
Microsoft evaluated with moderate confidence that the actor threatened in advance to determine whether it is the purpose of ejection Messenger users and then use zero day to distribute harmful loads and operating data for purposes.
Vulnerability in question Cve-2025-27920The vulnerability of the catalog that affects the 2.0.62 version, which allows remote attackers to access and execute arbitrary files. The question was address With its developers SRIMAX as of the end of December 2024 with version 2.0.63. The company, however, does not mention the lack that is exploited in the wild in its advisory.
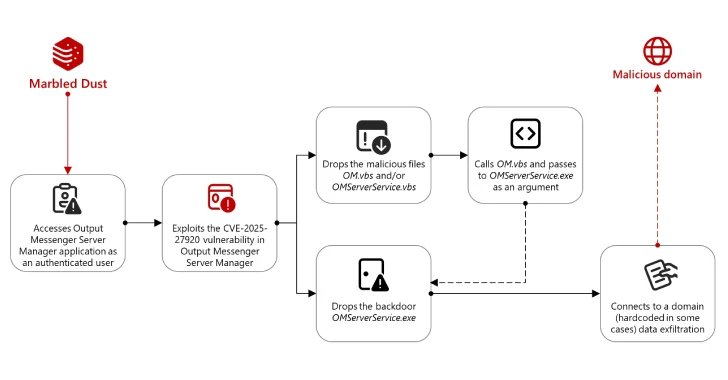
The attack network begins with the fact that the actor threats are accessed by the Servger Server Manager as an authentified user. Marble dust is believed to use methods such as DNS kidnapping or typical domains to intercept the credentials needed to authenticate.
The access is then abused to collect the Messenger conclusion credentials and use the CVE-2025-27920 to give up useful loads such as “om.VBS” and “omserverservice.vbs” to the server launch folder and omserverservice.exe.
In the next phase, the threatening actor uses “omserverservice.vbs” to cause “om.vbs” and “omserverservice.exe”, the latter of which is the back of the Golang, which contacts a solid domain (“Api.wordinfos (.) Com”
“On the client’s side, the installer highlights and performs both legitimate files outPutmessenger.exe, as well as omclientservice.exe, another back of Golang, which connects to the marble domain and control (C2),” Microsoft noted.
“This back first performs the connection check using the request to the C2 API.Wordinfos domain (.) Com. If this successfully, the second request is sent to the same C2 that contains information about the host name to clearly determine the victim.
In one case, the victim’s device with the Messenger client, installed by IP -Odars, which had previously been used by marble dust for a likely expressive data, participated.
The technological giant also noted that he discovered in the same version the second drawback, reflected the vulnerability of the scripts (XSS) (XSS) (in the same version (Cve-2025-27921) Although it states that it did not show evidence that he was armed with real attacks.
“This new attack signals a noticeable shift in the possibility of marble, while maintaining the sequence in their overall approach,” said Microsoft. “Successful use of the zero day feat suggests an increase in technical sophistication, and may also suggest that marble dust priorities have grown or that their operative goals have become more relevant.”