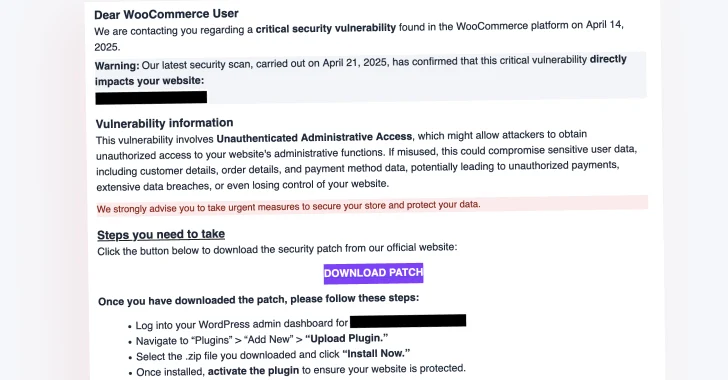
Cybersecurity researchers warn of a large -scale phishing campaign aimed at WooCommerce users with a fake security warning calling them to load a “critical patch” but instead deploy the back.
WordPress Patchstack’s security company called the activity as a complex and variant of another company observe In December 2023, this used fake Cve Ploy to violate sites that control the popular content management system (CMS).
Given the similarity of e -mail phishing baits, fake web pages and the same methods used to hide malware, it is believed that the last wave of the attack is either the work of the same threat actor, or this is a new cluster that carefully imitates the former.
“They declare IDN Homograph Attack To disguise yourself as an official WooCommerce “site, a security researcher – Note.
Financial Email recipients are calling for a “download patch” link to download and install the intended security fix. However, this redirects them to a fake WooCommerce market, located on the “WooComMėRce” domain (.) Complay the use of “ė” instead of “e”), where you can download the archive zip (“AuthbyPasse-update-31297-IDIP”).
The victims are then offered to install the patch because they install any ordinary WordPress plugin, effectively unleashing the following series of malicious action –
- Create a new user at an Administrator level with a difficulty username and randomized password after setting by accident named Cron’s assignment that works every minute
- Send HTTP to receive an external server request (“WooCommerce-Services (.) Com/WPAPI”) with the username and password, as well as URL infected site
- Send HTTP to receive the download request for the next stage of the embarrassed load from another server (“WooCommerce-Help (.) Com/Active” or “WooCommerce-API (.) Com/Active”
- Private a useful load to retrieve multiple web fellows such as PAS-FORK, P0WNY and WSO
- Hide the malicious plugin from the plugin list and hide the created administrator account
The pure result of the company is that it allows the attackers remote control over the sites, allowing them to introduce spam or sketch ads, redirect site visitors to fake sites, record a broken server in Botnet for DDOS attacks and even registered server resources as part of the drawing scheme.
Users are advised to scan your instances on suspicious plugins or administrator accounts, and make sure the software is relevant.