At least six South Korean organizations were aimed at the North Korea Perennial Related Group Lazarus As part of the company named Sinchol’s operation.
Activities are aimed at South Korea software, IT, financial, semiconductor production and telecommunications industries, according to a Caspersky report published today. The earliest evidence of the compromise was first discovered in November 2024.
The company included “a complex combination of strategy of watering and exploitation of vulnerability within South Korean software”, safety researchers sojun and Vasily Berdnikov – Note. “The lateral motion also used one -day vulnerability in the Innorix agent.”
The attacks were observed that pave the way for the famous Lazarus tools such as Intimidation. Agamomnon. Wagener. Signbtand Chair.
What makes these invasion are especially effective, this is likely to operate the Cross Ex Cross Exchangers, which is common in South Korea to ensure the use of Internet banking and government sites to support anti-class and digital signatures based on certificates.
“The Lazarus group shows a strong understanding of this specifics and uses a strategy oriented to South Korea, which combines vulnerabilities in such software with attacks on watering,” said the Russian supplier of cybersecurity.
Operating security deficiency in Innorix agent for lateral motion is characteristic of what similar approach was also adopted by Andariel Substrate In the past, Lazarus group is to deliver malware such as Volgmer and Andardoor.
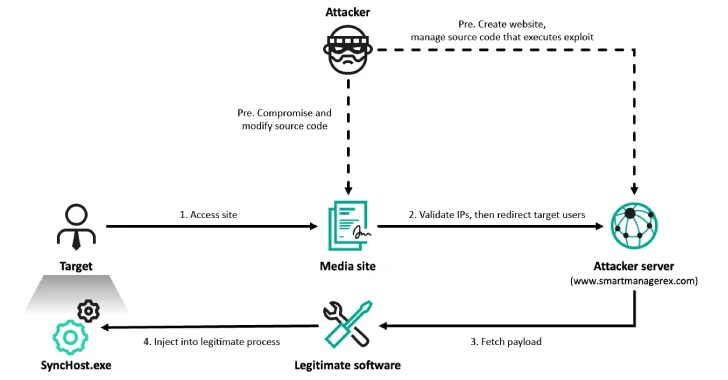
The starting point of the last wave of attacks is an attack for irrigation that has activated the deployment threats after the goals have visited various South Korean Internet. Visitors landed on the sites are filtered by means of the script on the server side before redirecting them to the domain controlled by the enemy to serve malicious software.
“We assess the average confidence that the redirect site may have fulfilled the harmful scenario, focusing on the potential deficiency in Cross Ex, installed on the target PC, and running malware,” the researchers said. “The scenario then ended in a legitimate synchost.exe and introduced into this process the Valiant ofgerneedle option”.
After the early stages, there is a sequence of infection, adopted two stages, using the threat and variety in the early stages, and then Signbt and Copperedge to establish persistence, conduct and provide tools of dumping accounts for compromised hosts.
Also deployed families of malware, such as LPECLIENT to profiling the victims and delivery of a useful load, as well as the bootloader, called Agamemenon to download and execute additional useful loads obtained from the server command and control (C2), simultaneously incorporating the technique of BP shutter to bypass the safety decisions.
One useful load loaded with Agamemenon is a tool designed to carry out lateral motion using a lack of security in the Innorix Agent file transfer. Casper said Since then has been secured Developers.
“It is expected that specialized attacks by Lazarus Group aimed at the supply networks in South Korea will continue in the future,” Kaspersky said.
“The attackers also make efforts to minimize the detection by developing new malware or improving existing malware. In particular, they introduce enhancements in communication with C2, team structure and how they send and receive data.”