Cybersecurity researchers detail about the vulnerability in Cloud Google (GCP) Cloudy composer The workpiece orchestration service that is based on Apache Air flow.
“This vulnerability allows the attackers with editing Cloud Build Herself – Note In a report that shared with Hacker News.
Disadvantage Confused featureThe vulnerability of the escalation privilege affecting the GCP cloud function, which the attacker can use to access other services and sensitive data in unauthorized order.
Disclosure takes place a few weeks after Tenable described in detail another vulnerability of escalation privileges in GCP Cloud Run, called Imserunner This can allow malicious actors to access container images and even make a malicious code – create cascading effects.
Like the Imagerunner, Convidescomposer is another example of the Jenga concept that inherit the security problem from one service to another when cloud services provides new services on existing ones.
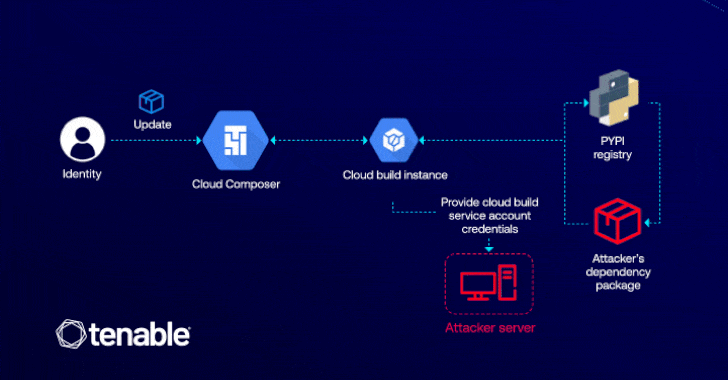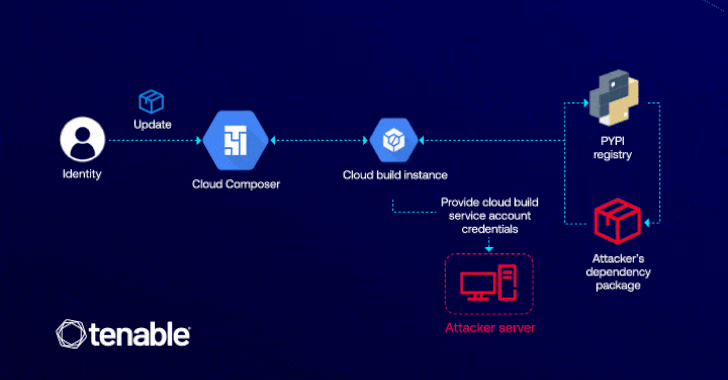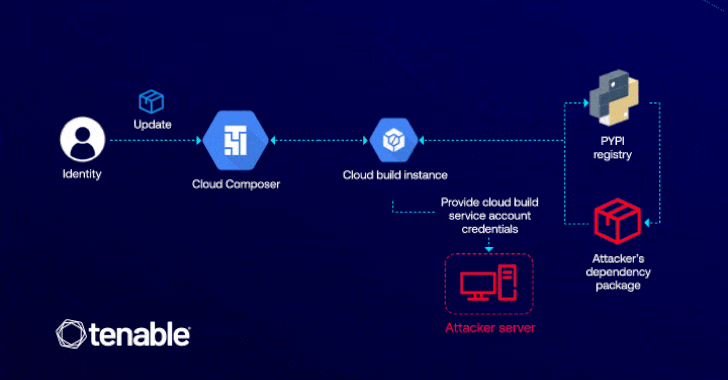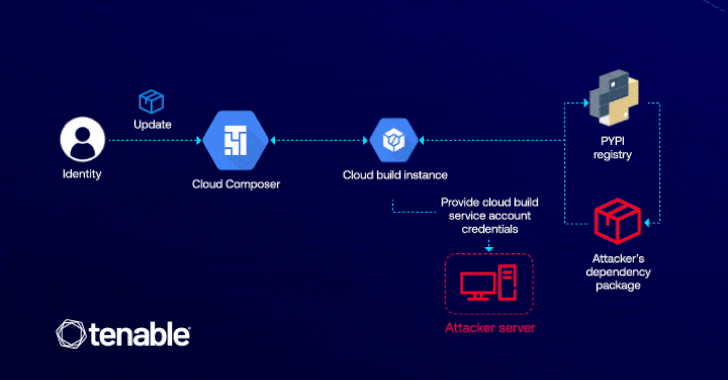
Operating loops on the attacker having a cloud composer’s medium to edit (ie, composer.environments.update), which can be used to introduce a malicious Python package (PYPI), which is able to enhance the privileges through the cloud assembly.
The attack is made possible by the fact that Cloud Composer allows users to install custom packages in their environment, allowing the enemy to perform an arbitrary code in the appropriate cloud Build copy using the installation scenarios in their malicious package.
“Computycomposer is confused because it exposes how the behind-the-scenes interactions between cloud services can be used through the escalation of privileges,” Matan explained. “In this case, the attacker only requires permission to update the cloud composer to access critical GCP services such as cloud storage and register of artifacts.”
Successful exploitation of the lack can allow the attacker to Siphon -sensitive data, disrupt services and deploy the harmful code within the CI/CD pipelines. In addition, it can pave the way to deploy the back, which can give constant access to compromised cloud conditions.
Following the responsible disclosure of Tenable information, Google has appealed to the vulnerability since April 13, 2025, turning off the Cloud Service account to install Pypi packages.
“Instead will be used an environmental account account”, Google – Note In a message on January 15, 2025. “Existing Cloud Composer 2 Wednesday, previously used by default Cloud Build services will change to use the Environment’s Service account.”
“Cloud Composer 2 Wednesday, created in versions 2.10.2, and later have this change. Cloud Composer 3 already uses an environmental account account and does not affect this change.”
Disclosure occurs when laboratories threatening varonis found vulnerability in Microsoft Azure, which could allow the actor threat with privileged access to Azure SQL Server to change configurations in a way that causes the data loss during the administrator’s action. Microsoft fully developed the issue as of April 9, 2025, after it reported it on August 5, 2024.
The company, according to the company, is related to the lack of a character restriction to limit the character to limit the character for the rules of the server firewall created using Transact-SQL (T-SQL).
“Manipulating the name of the Firewall Rules at the server level via T-SQL, the actor threats with the privileged access to Azure SQL Server may introduce the implant that, based on the specific actions of the user – Note.
“The influence of the actor of the threat that exploits this vulnerability can become a large -scale data loss on Azure’s victim.”
It also comes when Datadog Security Labs shed light on an error in the Microsoft Entra ID administrative units that could allow the attacker to prevent, removal, removal or shutdown, even the global administrator.
“The privileged attacker could use this error to protect the account under their control by preventing any Entra ID administrator,” Katie Knowles Research – Note. This included various tasks, such as password reset, cancellation of user sessions, users’ removal and user authentication methods (MFA).
The problem has since been recorded by the Windows manufacturer as of February 22, 2025 after the responsible disclosure of information on August 19, 2024.
In recent weeks, threatening subjects have been found, teaching their sights on websites located on Amazon Web Services (AWS) Elastic Compute Cloud (EC2), using fake vulnerabilities (SSRF) for metadata information.
“Metadata copies EC2 is a feature provided by AWS – Note. “It can expose information, such as public or private IP -Drass, instant instance and Iam credentials. In many ways, these are sensitive data interested in the attackers.”