The Chinese threatening actor known as the UNC5174 has been associated with a new company that uses a well -known malicious software called Leanlight and a new open source tool called Vheell to infect Linux Systems.
“Threat actors are increasingly using Open Source Tools in their arsenals for Cost-Effectiveness and Obfuscation to Save Money and, in this Case, Plausibly Blend in With The Pool of Non-State-Sponso Adversaries (EG, Script Kiddies), Thereby Making attribute even more diffiction, “Sysdig Researcher alessandra rizzo – Note In a report that shared with Hacker News.
“It seems particularly relevant for this particular Actor threateningLast year, which is linked to the Chinese government. “
UNC5174, its also called the utez (either uetus) was Previously documented Using Google Mandiant as operating security deficiencies in Screenceyconnect and F5 Big-IP software for delivery based on C Downloader ELF called Swinight, which is designed to obtain a GOLANG tunnel, which received Goheavy from infrastructure, tied to the conducted command (C2). Known as Supershell.
Also deployed in the attacks was Goreverse, a public posterior shell, written in a hormone that works on a safe shell (SSH).
French National Information Systems Agency (Ansi) Cyber Review Report For 2024, published last month, stated that he noticed an attacker who uses a similar shopping vehicle, as in the UNC5174 to equip security deficiencies in a cloud household appliance (CSA), such as Cve-2024-8963. Cve-2024-9380and Cve-2024-8190 To get control and execute an arbitrary code.
“This set of invasion is moderately and restrained is characterized by the use of penetration tools, largely available as an open source and is already publicly reported – the use of the Rootkit code,” Ansi said.
It is worth noting that both the snow world and vshell are capable Earning for Apple MacOSwith the latter spreads as a fake Authenticator cloudflare app as part of an even more flooded attack chain, according to Analysis of artifacts Downloaded to Wirustotal from China in October 2024.
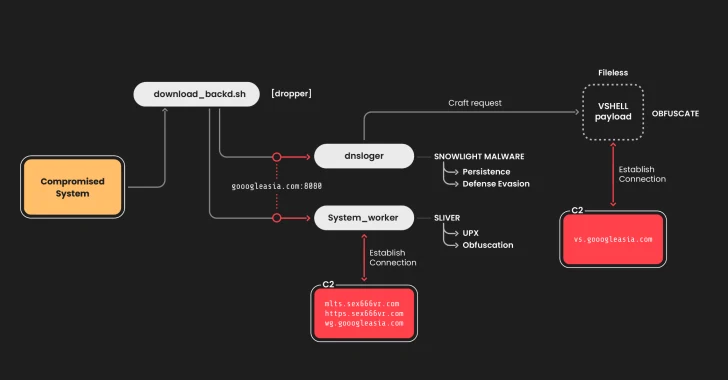
In the attack chain observed Sysdig at the end of January 2025, malicious snowmobile software acts as a drip for a disenfranchised, useful load called Vshell. The initial access vector used to attack is currently unknown.
In particular, the initial access is used to perform the malicious Basha (“Download_backd.sh”), which deployed two binary files related to snow light (DNSLOGER) and Flint (System_Worker), both of them used to set up perseverance and establish a C2 server.
The final stage of the attack provides Vshell Through the snow world with a specially designed request for the C2 server, which allows for remote management and further operation after the compromise.
“(Vhell) acts as a rat (Trojan remote), allowing it to be rapped to perform arbitrary commands and downloading or downloading files,” Ritz said. “Lyules and Vhell are a significant risk for organizations from their hidden and complex methods,” Sisdig said. “This is evidenced by the employment of WebSockets for teams and control, as well as a useful Vheell load.”
Disclosure is going on as Teamt5 disclosed that a group of hacking Chinese and Nexus probably used security deficiencies in IVanti’s instruments (Cve-2025-0282 and Cve-2025-22457) to gain initial access and deploy Notification malicious software.
According to Taiwanese cybersecurity, the attacks focused on many sectors that cover almost 20 different countries such as Austria, Australia, France, Spain, Japan, South Korea, Netherlands, Singapore, Taiwan, United Arab Emirates, United Kingdom and USA.
Results also Stut with charges from China that the US National Security Agency (NSA) launch The “expanded” cyber -post during Asian winter games in February, pointing to three agents of NSA for repeated attacks on important information in China as well as against Huawei.
“At the Ninth Asian Winter Games, the US government conducted cyberattacks on information systems and critical information infrastructure in the Hylongjiang,” the Ministry of Foreign Affairs Press Lin Jiang – Note. “This step causes this very much to threaten the safety of the critical information infrastructure of China, national defense, finance, society and production, as well as the personal information of its citizens.”