Recently disclosed security lack of Gladine Centrestack also affects his decision TriFox remote and cooperation, according to Hontress, with seven different organizations today.
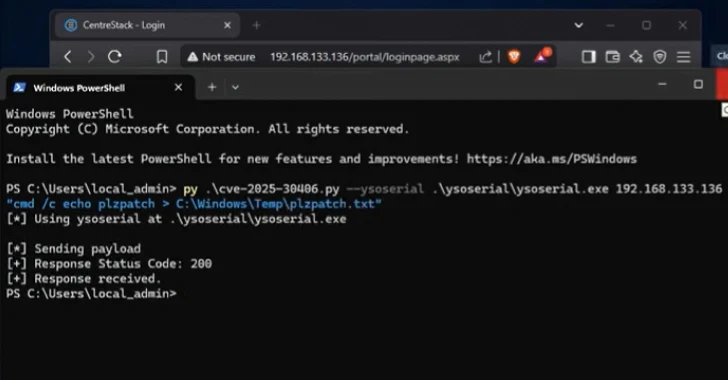
Tracked as Cve-2025-30406 .
It was considered at the center of the version 16.4.10315.56368, released on April 3, 2025. It is said that vulnerability was used as a zero day in March 2025, although the exact nature of the attacks is unknown.
Now, according to the hunting, also weakness affects the Gradinet TriFox To version 16.4.10317.56372.
“By default in previous versions of TriFox software there are the same hard crying keys in their configuration file, and they can be easily abused for performing remote code,” John Hammond, Chief Cybersecurity Researcher in Huntress, – Note In the report.
Teleometry data collected from its affiliate base showed that Centrestack software is set at approximately 120 end points and that seven unique organizations have affected the operation of the vulnerability.
The earliest signs of compromise date from April 11, 2025, 16:59:44 UTC. Attackers were observed using a lack of download and download Dll using a coded PowerShell scenario, an approach observed in The last attacks Use Lack of lackThen the lateral motion and installation of the meshcentral for remote access.
https://www.youtube.com/watch?v=-zpjygzdujmm
The hunter also stated that the attackers were identified as running PowerShell commands to perform various Meshagen listings. Given this, the exact scale and the ultimate goal of companies are currently unknown.
In light of active operation, it is important that Centrestack and TriFox users update their instances to the latest version to protect against potential risks.