Open PostgreSQL specimens are the goal of a current company designed to obtain unauthorized access and deploying cryptocurrency miners.
Wiz Wiz Cloud Security said the activity is a penetration recruitment that was first indicated by Aqua Security in August 2024 Pg_mem. The company was related to the “Wizard” track, which threatens as Jinx-0126.
“Since then, the actor threatens developed, introducing the methods of evading protection, such as the deployment of binary files with a unique hash on the target and performing a useful miner load, probably evading (platform Cloud Worker loads), which rely solely on the reputation of Hash Tikok – Note.
Wiz also showed that the company probably stated that there are more than 1500 victims today, which indicates that accidentally laid out general educational copies with weak or predictable powers are quite common to become a target for a conjunctural threatening attack.
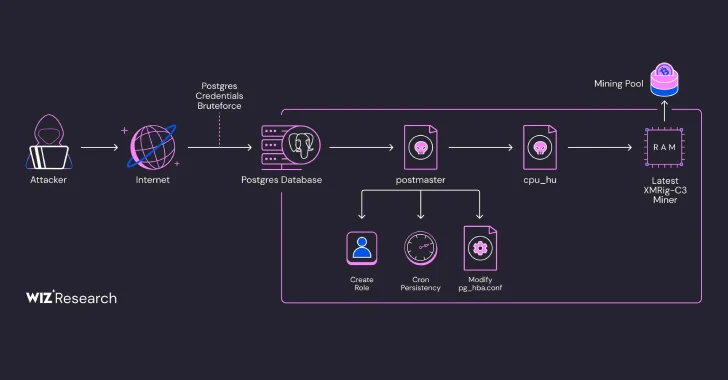
The most distinctive aspect of the company is the abuse of a copy … from the SQL team program to perform arbitrary shell on the host.
The access provided by the successful operation of the poorly customized PostgreSQL services is used to conduct pre -exploration and reduce the useful load on the basic 64, which in reality is the script of the shell, which kills the competing mines of cryptocurrencies and throws binary called PG_Core.
Also loaded on the server – is a clouded binary code that is in Golang which imitated Legisted PostgreSQL database server. It is designed to create perseverance on the host, using the work of Cron, create a new role with high privileges and write another binary called CPU_HU on the disk.
CPU_HU, on its part, uploads the latest version Xmig mines from gitHub and launches it without it without known technology called Linux called Memfd.
“The threat actor assigns to every sacrifice of unique prey,” the visas said, adding that he has identified three different wallets related to the actor. “Each wallet had approximately 550 workers. Together, it suggests that the company could use more than 1500 compromised machines.”