A campaign that penetrates legitimate sites with malicious JavaScript injections to promote Chinese gambling is continued, and approximately 150,000 sites are compromised.
“The actor threatened a little updated his interface, but still relies on IFRAME injection to show a full-screen circulation in the visitors’ browser,” C/Side Security Analyst Himanshu Anand – Note In a new analysis.
As of writing, there is More than 135 800 sites containing a useful load of JavaScript, according to Publicww statistics.
As documented Last month, the company’s security company includes infection with angry JavaScript sites, which is designed to kidnap the user’s browser to redirect site visitors to pages that promote gambling platforms.
The redirection has been found through JavaScript, located on five different domains (for example, “Zuizhongyj (.) Com”), which in turn serve the main useful load responsible for the recharge.
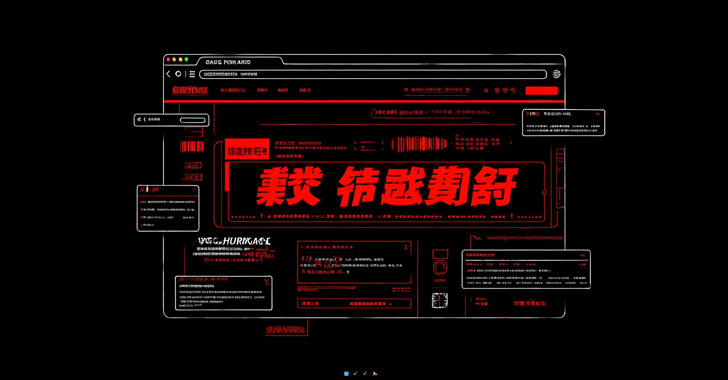
C/Side said there is also another company that entails injection scenarios and IFRAME elements in HTML, which represents legal rates such as Bet365 using official logos and branding.
The ultimate goal is to serve a full -screen lining using CSS, which causes malicious gambling when visiting one of the infected sites instead of the real web -based website.
“This attack demonstrates how the threat subjects are constantly adapting, increasing their reach and using new layers of exacerbation,” Anand said. “Such attacks on the clients are increasing and more and more results every day.”
The disclosure of information occurs when Godaddy has revealed details about the long -term surgery on malicious programs called Dollyway World Damination, which threatens more than 20,000 sites in the world since 2016. As of February 2025, more than 10,000 unique WordPress sites were victims of this scheme.
“The current iteration (…) is primarily focused on visitors of the infected WordPress via the retained redirect scripts that use the distributed network of the traffic direction (TDS) located on the impaired web -styities,” – Note.
“These scripts are redirected by site visitors to different pages of scam through road networks related to VextrioOne of the largest well -known networking networks that use sophisticated DNS methods, traffic distribution systems and domain generation algorithms to deliver malicious programs and scams on global networks. “
The attacks begin with the introduction of a dynamically generated scenario to the WordPress site, eventually redirecting visitors to Vextrio or Lospollos links. The lesson is also said to have used advertising networks as Screw to monetize traffic from broken sites.
Malicious injections on the server side are facilitated through the PHP code, inserted into the active plugins, and take measures to disable security plugins, removal of malicious administrator users and legitimate administrator powers to achieve their goals.
Since then, Godaddy has shown that Dollyway TDS has been using a distributed WordPress websites as TDS and Command-Control (C2), reaching 9-10 million monthly impressions. Except Litigation Traffic network.
Approximately in November 2024, as they say, Dollyway operators removed several C2/TDS servers, with the TDS scenario received URL -url from a telegram called Trafferredirect.
“Dollyway’s relationship violation with Lospolos means a significant turning point in this perennial company” Synegubko noted. “While the operators demonstrated a significant adaptation, quickly passing the alternative methods of monetization of the road, rapid changes in infrastructure and partial shutdown indicate a certain level of operational impact.”