Actor threats known as Encryption Exploits the recently concurrent security vulnerability in Microsoft Windows as a zero day to provide a wide range of malware families, including back and information theft such as Rhadamanthys and Ctealc.
“In this attack, the actor threatens .Msc files and multilingual – Note In the analysis.
Vulnerability in questionMmc) This can allow the attacker to bypass the security function at the local level. It was fixed The company earlier this month as patch update on Tuesday.
Trend Micro gave a feat nickname MSC Eviltwin, tracking the suspected Russian cluster of activity called Water Gamayun. Actor threats recently the subject of the analyzes Inspects and Outpost24 are also called larva-208.
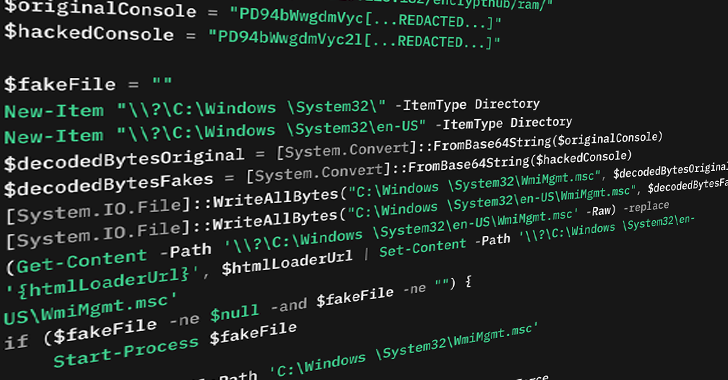
The CVE-2025-26633, according to its basis, uses the Microsoft Management Framework Console (MMC) to perform the malicious Microsoft console (.MSC) using PowerShell loading MSC Eviltwin Loader.
In particular, it provides for the creation of two .MSC names of the same name: one pure file and its analogue of the robbers, which is dropped in the same place but in the catalog called “en-US”. The idea is that when previously launched, MMC unintentions selects the malicious file and performs it. This is performed by using the MMC Multilingual Multilingual Interface (Muipath).
“By abusing the way MMC.exe uses Muipath, the attacker can equip Muipath En-US. The .MMSC, which causes MMC.exe to download this malicious file instead of the original file and executed without the victim,”-explained.
It was also noted that when taking the other two methods to run the malicious load in the infected system using .MMSC files –
- Use ExecuCteshellcommand MMC method to download and perform a useful load on the victim’s car, approach Previously documented Dutch cybersecurity campaign in August 2024
- With the help of Bulled trusted catalogs For example, “C: \ Windows \ System32” (note the blank blank) to bypass the user account (UAC) and give up
Trend Micro noted that the attack chains are probably starting with the Files Digitally Microsoft Installer Microsoft (MSI) boot, representing themselves to a legitimate Chinese software, such as Dingtalk or QQtalk, which is then used to obtain and perform a remote server loader. The actor is said to have the threat experimenting with these methods since April 2024.
“This company is under active development; it uses several delivery methods and custom useful loads designed to maintain persistence and theft of sensitive data, and then allocate it to command and control from the attackers (C&C),” said the stuck.