A new malicious program has been noted that use social engineering tactics R77.
Activities condemned Incomprehensible # bat According to Securonix, it allows the subject to threaten perseverance and elimination from detection on impaired systems. It is now unknown who is behind the company.
Rootkit “has the ability to cry or mask any file, registry key or task starting with a specific prefix,” – Den Iuzvyk and Tim Peck Researchers – Note In a report that shared with Hacker News. “It is focused on users or masking as legitimate software downloads, or through fake Social Engineering.”
The company is designed mainly for orientation to English -speaking persons, especially the US, Canada, Germany and the UK.
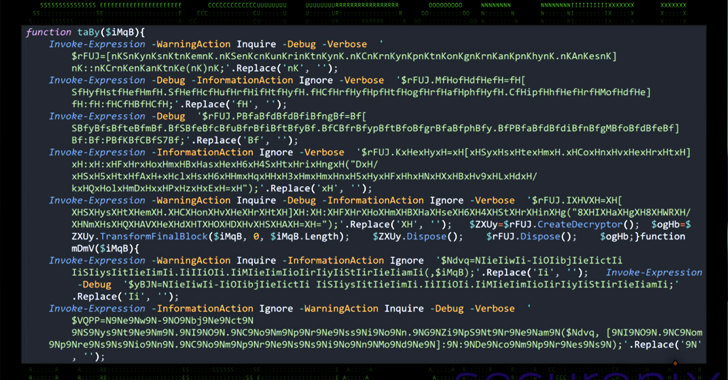
The indefinite#the bat gets its name from the fact that the starting point of the attack is a persistent Windows Party scenario, which, in turn, performs PowerShell commands to activate a multi -stage process that ends with Rootkit deployment.
At least two different initial access routes were discovered to force users to execute malicious package scenarios: one that uses shame Clickfix Strategy by sending users to a fake Cloudflare Captcha check page and the second method that uses ads with malicious programs as legitimate tools such as Tor browser, VoIP software and messaging customers.
Although it is unclear how users are lured into the BOOBY software, it is suspected that it includes tested approaches such as Malvertising or Aptimization Vearch (SEO) poisoning.
Regardless of the method used, the useful load of the first stage is the archive that contains a package scenario that then causes the PowerShell team to give up additional scripts, make the Windows registry modifications and set up planned tasks for sustainability.
“Malicious programs keep the enchanted scenarios in the Windows Register and ensures the fulfillment of the planned tasks, allowing it to work in the background,” the researchers said. “In addition, it changes the system of the system registry to register a fake driver (Acpix86.sys), further built into the system.”
Expanded throughout the attack is .Net a useful load that uses tricks to avoid detection. This includes controlling control, rows encryption and use of functional names that mix Arab, Chinese and special characters.
Another useful load loaded using PowerShellAmsi) Fixing to the bypass antivirus detection.
Useful .Net load ultimately responsible for refusing the Rotorkit mode called “Acpix86.sys” to the “C: \ Windows \ System32 \” folder, which is then launched as a service. Also comes a user mode that Rootkit is called R77 to set up a persistence on the host and hide the files, processes and registry keys that match the template ($ NYA-).
Malicious software additionally periodically monitors the activity of the clipboard and team history and saves them in hidden files for a likely exports.
“The indefinite#the bat demonstrates a very evil attack chain, using exacerbation, stealth methods and API connection to keep on broken systems, evading detection,” the researchers said.
“From the initial execution of the enchanted package script (Install.bat) to the creation of the planned tasks and scripts that store the register, malware provides persistence even after restart. Introduction to such critical processes as Winlogon.exe, it manipulates the behavior of the process to further complicate the detection.”
The conclusions come as a cooffs minute The Microsoft Copilot Fake Company, which uses phishing sheets to translate users into a fake target page for artificial intelligence (AI), which is designed for users’ accounts and two -factor authentication codes (2FA).