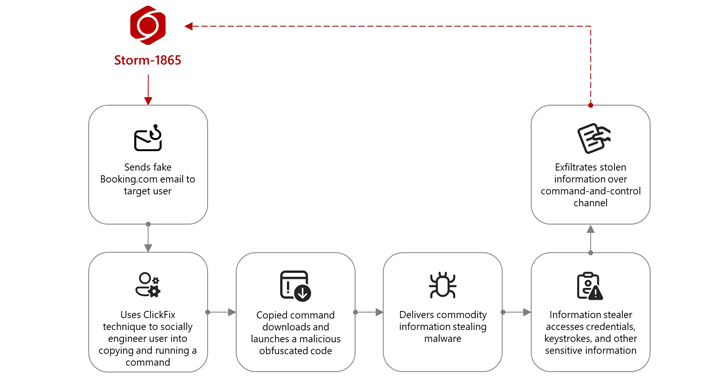
Microsoft shed light on the current phishing campaign aimed at the hospitality sector by presenting itself to the Booking.com online tourist agency, using an increasingly popular social engineering technique called Clickfix for malware.
According to the technological giant, it began in December 2024 and operates for the purpose of conducting financial frauds and thefts. This is the tracking company nicknamed Storm-1865.
“This phishing attack is specifically aimed at the Hospitality Organization in North America, Oceania, Southern and Southeast Asia, as well as North, South, Eastern and Western Europe, which are most likely – Note In a report that shared with Hacker News.
The Clickfix technique has become widespread In recent months, when it is cheating on users to perform malicious software under the guise of correction of the alleged (ie non -existent) errors, copying, inserting and running deceptive instructions that activate the infection process. It was first discovered in the wild in October 2023.
The attack sequence begins with the fact that the Storm-1865 sends a malicious electronic message to a purposeful person about the negative review left by the guest at booking.com and asks them to “feedback”. The message also includes a link or attachment of a PDF containing one that seems to send the recipients to the booking site.
However, in reality, pressing it is the victim on the fake Kapch check page, which is blocked on “a subtly visible background designed to imitate the legitimate booking.com”. By doing this, the idea is to give a false sense of safety and increase the likelihood of successful compromise.
“Fake CAPTCHA is where the social engineering technique is used on the web page to download the malicious load,” Microsoft said. “This technique instructs the user to use the keyboard combination to open the Windows launch window, then insert and run the command that the web page adds to the clipboard.”
A team, in a nutshell, uses legitimate binary mshta.exe to give up a useful load on the next stage, which includes various commodity malware, such as Xworm, Lumma Ctyler, Venomrat, Asyncrat, Danabot and Netsupport Rat.
Redmond said it was previously noted that the Storm-1865 was targeted by buyers using e-commerce platforms with phishing reports that lead to fraudulent payment web pages. Thus, the inclusion of ClickFix technique illustrates a tactical evolution designed to pass the usual security measures against phishing and malware.
“The actor of the threat that Microsoft monitors both the Storm-1865, covers the cluster of activity conducting phishing campaigns, leading to theft of payment and falsification of charges,” he added.
“These companies are ongoing with an increase in volume at least at the beginning of 2023 and include messages sent through suppliers platforms such as online tourist agencies and e-commerce platforms as well as e-mail such as Gmail or iCloud Mail.”
The Storm-1865 is only one of the many companies that has taken Clickfix as a vector to distribute malware. This is the effectiveness of this technique that even Russian and Iranian national groups love APT28 And Muddywater took it to lure his victims.
“In particular, the method will take advantage of a person’s behavior: presenting a plausible” solution “to a perceived problem, attackers move the load to the user, effectively sending to many automated protection,” Group-IB – Note In an independent report published today.
One of these companies recorded by the Singaporean Cybersecurity Company provides the use of Clickfix to refuse a download called Smokesaber, which then serves the Lumma stealing. Other companies use violations, SEO poisoning, GitHub problems, as well as spam forums or social media sites with links to ClickFix pages.
“Clickfix technique means evolution in competition strategies for social engineering, using the trust of users and the browser functionality to deploy malware,” said Group-IB. “The rapid adoption of this method, both cyber -veils and APT, emphasizes its effectiveness and low technical barrier.”
Some other clickfix companies that have been recorded below –
Various mechanisms for infection of the theft of Lumma are also manifested by the detection of another company that uses gitub gums that represent artificial intelligence (AI) to deliver the theft through a loader called Smartloader.
“These malicious shelters are masked into non-standard tools, including gaming cleaning, hacked software and cryptocurrency utilities,” Trend Micro – Note In an analysis published earlier this week. “The company encourages the victims with the promises of free or illegal unauthorized functionality, pushing them to download postal files (eg, releat.zip, software.zip).
The operation serves to emphasize how the threatening subjects abuse confidence related to popular platforms such as GitHub to distribute malware.
The conclusions come as Trustwave talked in detail about a phishing company by email that uses baits related to accounts Strelastalerevaluated to manage a single threatening actor named Hive0145.
“Strelastealers samples include custom multilayered exacerbations and smoothing code flow to complicate its analysis,” the company – Note. “It was reported that the actor threatened potentially developed a specialized cryptor called” Star Loader “, in particular, will be used with the shooter.”