Subgroup in a shameful Russian state group known as Pepperner was associated with a long -standing initial access operation called Badpilot, which stretched around the world.
“This subgroup conducted a globally diverse compromise of the infrastructure that stands on the Internet to allow SEASHELL snowstorms to be stored on high values and maintain individual network operations,” Microsoft intelligence team is threatened. – Note In a new report that shared with Hacker News on the eve of the publication.
The geographical distribution of the initial access goals includes all North America, several European countries, as well as others, including Angola, Argentina, Australia, China, Egypt, India, Kazakhstan, Myanmar, Nigeria, Pakistan, Turkey and Uzbekistan.
Over the past three years, development means a significant expansion of the hacking group that is known to concentrate around Eastern Europe – –
- 2022: Energy, retail, educational, consulting and agricultural spheres in Ukraine
- 2023: sectors in the US, Europe, Central Asia and the Middle East, which provided material support for the war in Ukraine or were geopolitically significant
- 2024: Subjects in the USA, Canada, Australia and UK
Sandwest is monitored by Microsoft, nicknamed Seashell Blizzard (formerly Iridium), as well as a wide cybersecurity community under the names of APT44, Blue Echidna, Frozenbarents, Grey Tornado, Iron Voking, Razing Ursa, Telebots, Uc-000 and Voodo Min. Active, at least 2013, the group is estimated, which will be related to the 74455 division in the Main Directorate of the General Staff of the Russian Federation (GR).
The competition team was described Using Google Mandiant as “very adaptive” and “promptly mature” threatening actor involved in espionage, attack and affects surgery. It also has mounting results devastating and devastating attacks Against Ukraine over the last decade.
Companies established by Sandworm as a result of the Rus-Ukrainian War used glass cleaning (Killdisk AKA Hermeticwiper), pseudo-Ren Program (Prestige AKA PRESSTEA), and the rearCoffee) In addition to families malicious programs that allow the subject threats to support Sustainable remote access to infected hosts through Darkcrystal rat (AKA DCRAT).
It was also noted that it is based on various Russian companies and criminal markets for the source and maintain their offensive capabilities, emphasizing a a growing trend Cybercrimity that contributes to the hacking that supports the state.
“The group used criminal tools and infrastructure as a source of disposable capabilities that can be operated in short period without urgent communication with past operations,” Google Group GTIG (GTIG) – Note In the analysis.
“Ever since a full -scale invasion of Ukraine in Russia, APT44 has increased the use of such tools, including malware, such as Darkcrystal Rat (DCRAT), Warand Sharply (“Rhadamanthys Cteeler”), and the infrastructure for hosting, for example, is stipulated by a Russian -speaking actor “Yalisanda”, which is advertised in cyber -centered communities. “
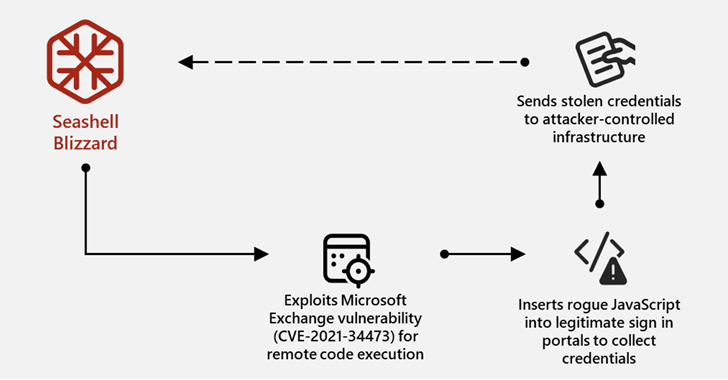
Microsoft said the Sandworm subgroup has been operating at least from the end of 2021, using various well -known security deficiencies to obtain initial access with the next series of action after operation aimed at collecting powers, achieving team execution and support for lateral motion.
“The observed operations after the initial access indicate that this campaign allowed SEASHEll snowstorms to access global goals in sensitive sectors, including energy, oil and gas, telecommunications, delivery, weapons production, in addition to international governments,” the technology giant said.
“This subgroup was allowed a horizontally scaled opportunity, backed up by published exploits that allowed SEASHELL BLIZZard to identify and compromise the many systems that exit the Internet in a wide range of geographical regions and sectors.”
Since the beginning of last year as they sayCve-2014-1709) and Fortinet Forticlient EMS (Cve-2023-4878) Eat targets in the United Kingdom and the USA.
The attacks conducted by the subgroup provides a combination of both conditionally pathogenic “attacks” and prayers and purposeful invasion designed to maintain disorderly access and perform the following actions to expand access to the network or obtain confidential information.
It is believed that a wide range of compromises offers SEASHELL BLIZZard a way of performing constantly developing Kremlin’s strategic goals, which allows hacking to hack horizontally scale its activities in different sectors when new feats are revealed.
The subgroup today has been used by eight different well -known security vulnerabilities
Successful fixing is changing the actor threats that establishes stability through three different methods –
- February 24, 2024 – present: Deploying legitimate software for remote access, such as ATEATOP ATEATOP Agent, in some cases abusing access to additional useful loads to obtain accounts, data exports and other access tools, such as Openssh and customer system that will be Available through the Tor Anonymity Network
- End of 2021 – present: Deploying a web-barrel called Localolive, which allows you to control the team and control, and serves pipes for greater load such as tunnel utilities (eg, chisel, plink and RSOCSTUN)
- End 2021 – 2024: Following modifications online (OWA) Login on the JavaScript code pages, which can gather and highlight back into real-time actor, and change the DNS A-record configuration, probably the service
“This subgroup, characterized in the broad organization of Blizzard Seashell Blizzard its almost Global Reach, is an extension both in the geographical target conducted by Seashell Blizzard and in its operations,” Microsoft said.
“At the same time, far -reaching methods of Access Seashell Blizzard are likely to offer Russia extensive opportunities for niche operations and activities that will continue to remain valuable in the medium term.”
Development occurs when the Dutch Cybersecurity Company Eclecticiq has linked the Sandworm group to another company that uses pirate Microsoft Key Management Service (Km is km.) Activators and fake Windows updates to provide a new Backberry version, booty -based Go, which is responsible for receiving and performing a useful load in the second stage from the remote server.
Ollies for a return order, usually delivered in the files of mounting heronized and rigidly coded to execute the executable file. The ultimate goal of the company is deliver Darkcrystal rat.
“Ukraine’s great dependence on shocked software, including in government agencies, creates the main surface of the attack,” Horde Bucca’s security researcher – Note. “A lot of users, including businesses and critical structures, turned to Pirate software From unverified sources, giving opponents such as Sandworm (APT44), the main opportunity to bury malicious software in widely used programs. “
Further infrastructure analysis revealed a previously unregistered RDP-Redp Codenen Kalambur, which is disguised in Windows update, and uses Tor for teams and control, as well as to deploy OpenSSH and incorporating remote access protocol (RDP) in port 3389.
“Using the Trajanized Software to penetrate the IS, Sandworm (APT44) continues to demonstrate its strategic purpose of destabilizing Ukraine’s critical infrastructure in support of Russian geopolitical ambitions,” Bakeka said.