Cybersecurity researchers have found a bypass for the NVIDIA container’s safety vulnerability, which can be used to escape the container and gain full access to the main host.
New vulnerability is tracked as Cve-2025-2359 (CVSS assessment: 8.3). This affects the following versions –
- Nvidia Container Toolkit (all versions up to 1.17.3) – recorded in version 1.17.4
- GPU Nvidia operator (all versions up to 24.9.1) – recorded in version 24.9.2
‘NVIDIA container’s tools for Linux contains time of use (Bakery) Vulnerability when used with the default configuration where a container image can access the host file system, “the company said on Tuesday.
“The successful feat of this vulnerability can lead to the code, refusal to service, escalation of privileges, disclosure and data fraud.”
https://www.youtube.com/watch?v=om5xyzkeoak
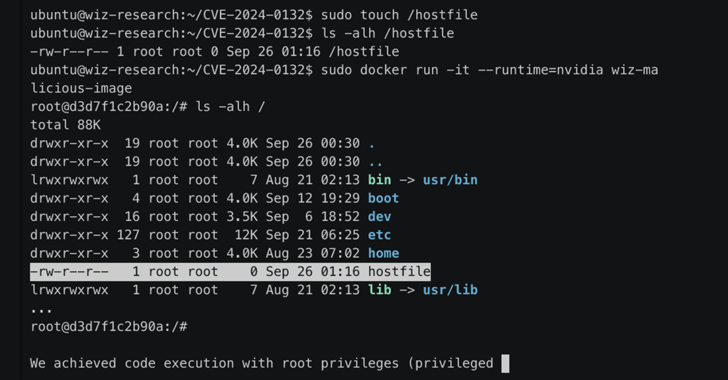
Wiz wiz that cloudy safety that general Additional technical specificity of this deficiency stated that this is bypass for another vulnerability (Cve-2024-0132CVSS assessment: 9.0), which was addressed to Nvidia in September 2024.
In a nutshell, the vulnerability allows the bad actors to install the hoste root system in the container, giving them unobstructed access to all files. In addition, access can be used to launch privileged containers and reaching full compromise of the host through the Unix socket.
Wiz Shir Tamari, Ronen Shustin and Andres Riancho Researchers have stated (ie root catalog) on a way within “/USR/lib64.”
While access to the host file system provided by the container is only read, this restriction can be bypassed by interacting with unix sockets to spawns new privileged containers and gain unlimited access to the file system.
“This elevated access levels also allowed us to control network traffic, renew active processes and perform a number of other operations at the host level,” the researchers said.
In addition to the upgrade to the latest version, Nvidia Container Tools are recommended not to disable “-no-Cntlibs” flag Under production conditions.