Microsoft warns of a dangerous practice in which software developers include publicly disclosed ASP.Net keys from publicly available resources, thus investing their applications into the path of attackers.
The Technological Giant Intelligence Team stated that it was observing limited activity in December 2024, which included an unknown threat actor using the ASP.Net’s public static key for imposing malicious code and delivery Godl Frame after operation.
He also noted that he identified more than 3,000 publicly discovered keys that could be used for these attacks View the Infrosting Codes.
“While many previously known injection code injection has used compromised or stolen keys that are often sold on dark web forums, these publicly revealed keys can pose a higher risk as they are available in multiple code In the development code without modification, “Microsoft – Note.
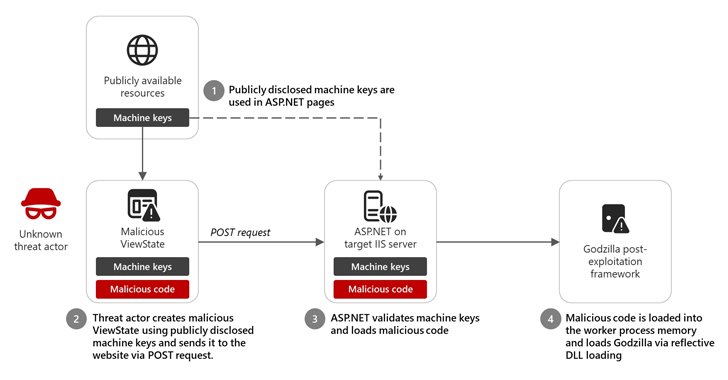
ViewState is a method used as part of ASP.net to save pages and controls between the backs. This may also include applications specific to the page.
“By default, data viewing is stored on the page in the hidden field and coded by coding Base64,” Microsoft notes in its documentation. “In addition, the hash data has a state -of -the -art data view using the machine authentication key (Mac). The hasha value is added to the coded view data, and the resulting string is stored on the page.”
When using the hash value, the idea is that the data condition is not spoiled and fake malicious subjects. Given this, if these keys are stolen or made available to unauthorized third parties, it opens the door to the script when the actor threats can use the keys to send a malicious request and execute an arbitrary code.
“If the request is processed by the time of the ASP.net on the target server, ViewState is transcribed and successfully confirmed as the correct keys are used,” Redmond said. “The malicious code is then loaded into the memory of the workflow and is performed, providing the remote code threat on the target web server IIS.”
Microsoft provided List of Hesh values For publicly disclosed by car keys calling customers checkup them against machine keys used in their environment. He also warned that in case of successful exploitation, publicly revealed keys would simply rotate the keys, as the threatening participants may have already set persistence on the host.
To mitigate the risk provided by such attacks, it is recommended that you not copy the keys from public sources and regularly turn the keys. As an additional step on curbing Microsoft threat subjects, she said she had removed key artifacts from “limited cases” when they were included in the documentation.
Development comes when the company Cloud Aqua Aqua revealed the details OPA Grakeeper Outbound that can be used for unauthorized actions in the Kubernetes environment, including the deployment of unauthorized drawings.
“In the K8sallowedrepos policy, the risk of security arises from how the logic rego is written in the ConstrainTemplate file,” Kadkoda Kadkoda researchers and Asaf Morara. – Note In the analysis that shared with Hacker News.
“This risk is further enhanced when users determine the values in the YAML limit, which do not match how the logic rego processes them. This inconsistency can lead to bypass, which makes restrictions ineffective.”