Cybersecurity researchers have discovered a company aimed at Microsoft advertisers with Bogus Google Ads aimed at transferring them to phishing pages capable of collecting their powers.
“These malicious ads that appear in Google are designed to kidnap users entry to access Microsoft’s advertising platform,” Jérôme Segura, Senior Malware Director, – Note In the report on Thursday.
The conclusions came a few weeks after cybersecurity expose A similar company that used Google Sponsored Advertising to orientation to people and businesses through the search giant advertising platform.
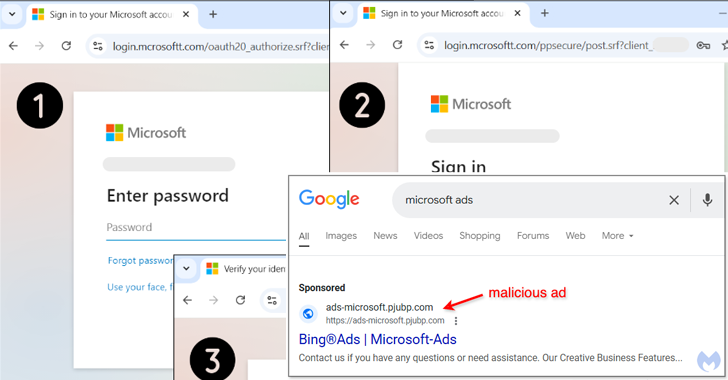
The latest set of attacks is focused on users looking for terms such as “Microsoft ADS” in search of Google, hoping to deceive them, pressing the malicious links provided in the form of sponsored ads on the search results pages.
At the same time, the subjects behind the company use several methods to evade safety tools. This includes the redirection of traffic that comes from VPN on the fake marketing site. The site visitors also serve Cloudflare problems trying to filter the boots.
Last but not less important, users trying to visit the final target page (“ADS.MCROSOFTT (. rickrolled Reducing them in a video from YouTube related to the famous Internet meme.
The Phisching Page is a similar version of its legitimate analogue (“ADS.Microsoft (.) Com”) designed to capture the victim’s accounting data and two-factor authentication codes (2FA), giving the attackers the opportunity to hold their accounts.
Malwarebytes said it had revealed additional phishing -infrastructure aimed at Microsoft’s credentials, which have been coming up to several years, believing that the company has been going on for a while, and that it may also be aimed at other advertising platforms such as Meta.
Another characteristic aspect is that most phishing domains are either located in Brazil, or there is a Brazilian upper -level domain “. tld.
The Hacker News appealed to Google to comment.
Strike attacks are advocating USPS
The disclosure of information stems from the appearance of a phishing company SMS, which uses unsuccessful baits shipping packages to only focus on mobile users, pretending to be US (USPS) postal service.
“This company uses sophisticated social engineering tactics and have never seen burglary to provide malicious PDF files aimed at stealing and compromising sensitive data,” Zimperium Zlabs Artega Arteg – Note In a report published this week.
Messages call on the recipients open the cover file PDF to update your address to complete the delivery. The PDF document provides a “Press Update” button that sends the victim to the Phishing USPS web page where they are asked to enter your mailing address, email address and phone number.
The Phishing Page is also equipped to collect payment card data under the guise of the service for refurbishment. Then the entered data is encrypted and transmitted to a remote server under the control of the attacker. As much as how much 20 malicious PDF and 630 Phishing Pages were found within the campaign, which testifies to a large -scale operation.
“PDFs used in this company, built -in links to the standard /URI buttons, making it more complicated to extract the URL during the analysis,” the Ortega said. “This method allowed the famous malicious URL -url PDF files to bypass multiple definition decisions.”
Activities are a sign that cybercrime uses security gaps on mobile devices to pull out social engineering attacks that take advantage of users’ trust in popular brands and official communication.
Similar attacks with USPS topics also used the Apple IMESSAGE to provide phishing pages, technology that is known Throwing triad.
Such messages are also deftly trying to bypass the security measure in the IMessage, which does not allow the links if the message is not from the famous sender or from the account which user is in charge of. This is done by turning on “Please reply to Y” either “please respond to 1 message, trying to disable the built-in phishing-defense IMessage.
It is worth noting that this approach was previously associated with the specified set of phising tools as services (Phaas) Darkulaused for extensive focus on postal services such as USPS and other created organizations in more than 100 countries.
“The scammers built this attack relatively well, and so they are so often seen in the wild,” Kain’s hunt – Note. “Simple truth, it works.”