A group of scientists has revealed details of more than 100 security vulnerabilities that affect the LTE and 5G introduction that can be used by the attacker to disrupt access to the service and even fixed in the main cellular network.
The 119 vulnerabilitiesAppointed 97 unique CVE ID, cover seven LTE – Open5gs. Magma. Openair interface. Atonate. Sd-core. NEXTEPC. SRSR – and three 5G – Open5gs, Magma, Openairinterface, according to researchers at Florida University and North Carolina State University.
The conclusions were described in detail in a study called “Ransacked: Domain-informed approach for Fuzzing LTE and 5G Ran-Core Interfaces”.
“Each of the> 100 vulnerabilities below can be used to constantly violate the entire cellular communication (telephone calls, messaging and data transmission) at the level of the whole city,” the researchers said.
“The attacker can continuously remove the Mobility Management Entity (MME) or Access and Mobility Management Function (AMF) on the LTE/5G network, respectively, simply sending one small network package as a non-aid user (without SIM card). required). “
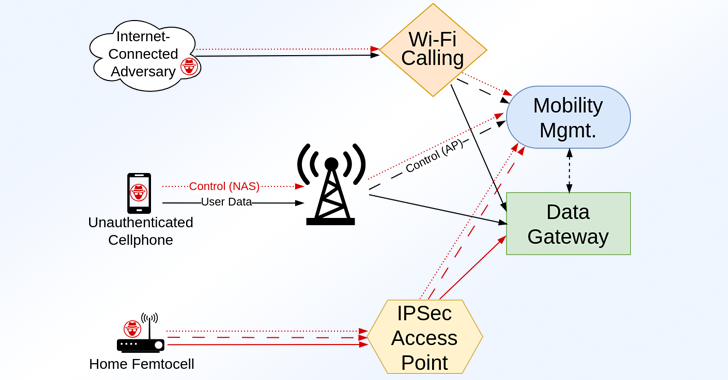
The opening is the result of a Exercise by phasingRelated to Ransacked by researchers against the radio network (Wound) – the main interfaces that are able to take the introduction directly from mobile phones and base stations.
Researchers have said that some revealed vulnerabilities are related to the overflow of the buffer and memory damage that can be used to hack the main cellular network, and use this access to monitor the mobile phone location and connection information for all city level subscribers. Purposeful attacks on specific subscribers, as well as further malicious actions on the network itself.
Moreover, the identified deficiencies fall into two broad categories: those that can be used by any non -austean mobile device, and those that can become an enemy weapon who hacked base station or A fumtosot.
Of the 119 revealed vulnerabilities, 79 were found in the MME, 36 implementations in AMF and four in SGW. Twenty-five drawbacks lead to Non-Aaccess Stratum (NAS) ATTO attacks that can be carried out using any mobile phone.
“The introduction of Femetasot for home use, and then more easily available GnodeB base stations in 5G deployment, is a further shift in security dynamics: where the Ran’s physically blocked equipment is now openly exposed to physical threats,” the study noted.
“Our work explores the consequences of this last area, allowing effective phasis -interfaces, which have historically been indirectly safe, but now face direct threats.”