A previously undocumented Advanced Persistent Threat Group (APT) with China has been named PlushDaemon was linked to a supply chain attack targeting a South Korean virtual private network (VPN) provider in 2023, according to new ESET findings.
“The attackers replaced the legitimate installer with one that also deployed the group’s proprietary implant, which we called SlowStepper, a multi-functional backdoor with a toolkit of over 30 components,” said ESET researcher Facunda Muñoz. said in a technical report shared with The Hacker News.
PlushDaemon is believed to be a China-related group that has been active since at least 2019 and targets individuals and entities in China, Taiwan, Hong Kong, South Korea, the United States, and New Zealand.
Central to its operation is a special backdoor called SlowStepper, which is described as a large toolkit consisting of about 30 modules programmed in C++, Python and Go.
Another important aspect of its attacks is hijacking legitimate software update channels and exploiting vulnerabilities in web servers to gain initial access to the target network.
Slovak cyber security company said that in May 2024. noticed malicious code embedded in the NSIS installer for Windows downloaded from a VPN software vendor’s website called IPany (“ipany(.)kr/download/IPanyVPNsetup.zip”).
The rogue version of the installer that was removed from the website is designed to remove the legitimate software as well as the SlowStepper backdoor. It is currently unclear who the exact target of the supply chain attack is, although any individual or entity downloading the mined ZIP archive could have been at risk.
Telemetry data collected by ESET shows that several users attempted to install trojanized software on networks associated with a semiconductor company and an unknown software development company in South Korea. The oldest victims were recorded in Japan and Chia in November and December 2023, respectively.
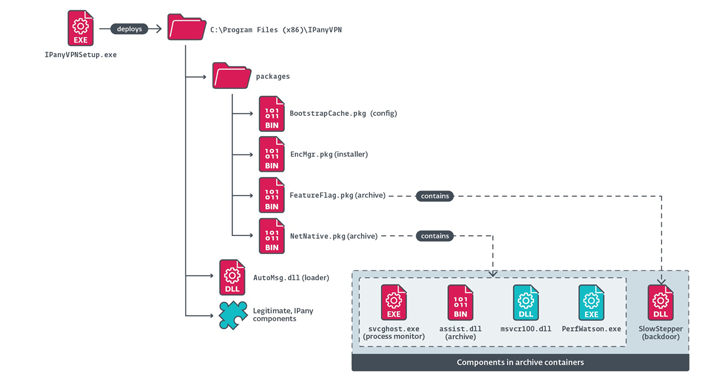
The attack chain starts with the execution of the installer (“IPanyVPNsetup.exe”), which continues to install security on the host between reboots, and starts the loader (“AutoMsg.dll”), which in turn is responsible for running shellcode that loads another DLL (” EncMgr.pkg”).
The DLL then extracts two more files (“NetNative.pkg” and “FeatureFlag.pkg”) which are used to load the malicious DLL file (“lregdll.dll”) with “PerfWatson.exe”, which is a renamed version of the legitimate utility command line file called regcap.exe, which is part of Microsoft Visual Studio.
The final purpose of the DLL is to load the SlowStepper implant from the winlogin.gif file located in FeatureFlag.pkg. SlowStepper is believed to be in the works since January 2019. (version 0.1.7), the latest iteration (0.2.12) was compiled in June 2024.
“Although the code contains hundreds of features, the specific variant used in the IPany VPN software supply chain hack appears to be version 0.2.10 Lite, according to the backdoor code,” Munoz said. “The so-called ‘lite’ version really contains fewer features than other previous and newer versions.”
Both the full and lite versions use an extensive set of tools written in Python and Go that allow data collection and covert surveillance through audio and video recording. The tools are said to have been hosted on a Chinese code repository platform GitCode.
For Command and Control (C&C), SlowStepper creates a DNS query to retrieve a TXT record for the domain company 7051.gsm.360safe(.) to one of three public DNS servers (114DNS, Google and Alibaba Public DNS). ) to obtain an array of 10 IP addresses, from which one is selected to be used as a C&C server to handle operator-issued commands.
“If it fails to connect to the server after a number of attempts, it uses gethostbyname API on the st.360safe(.)company domain to obtain the IP address bound to that domain and uses the resulting IP as a backup C&C server,” Munoz explained.
The commands work in a wide range, which allows you to capture comprehensive system information; execute the Python module; delete certain files; run commands through cmd.exe; list the file system; downloading and executing files; and even delete yourself. A rather unusual feature of the backdoor is to activate the user shell when receiving the “0x3A” command.
This gives an attacker the ability to execute arbitrary payloads hosted remotely (gcall), update backdoor components (update), and run a Python module on the compromised machine (pycall), the latter of which downloads a ZIP archive from the GitCode account containing a Python interpreter and a library for launch to collect interesting information –
- Browserwhich collects data from web browsers such as Google Chrome, Microsoft Edge, Opera, Brave, Vivaldi, Cốc Cốc browser, UC Browser, 360 Browser and Mozilla Firefox
- Camerawhich takes pictures when the camera is connected to the hacked machine
- CollectInfowhich collects files with the appropriate extensions .txt, .doc, .docx, .xls, .xlsx, .ppt and .pptx, as well as information from programs such as LetsVPN, Tencent QQ, WeChat, Kingsoft WPS, e2eSoft VCam, KuGou, Oray Sunlogin and ToDesk
- Decodewhich downloads a module from a remote repository and decrypts it
- DingTalkwhich collects chat messages from DingTalk
- Downloadwhich downloads non-malicious Python packages
- FileScanner and FileScannerAllDiskwhich scans the system for files
- getOperaCookiewhich receives cookies from the Opera browser
- A location that receives the computer’s IP address and GPS coordinates
- qpasswhich collects data from Tencent QQ browser (probably replaced by qqpass module)
- qqpass and Webpasswhich collects passwords from Google Chrome, Mozilla Firefox, Tencent QQ Browser, 360 Chrome and UC Browser
- Screen recordingwhich records the screen
- Telegramwhich collects data from Telegram
- WeChatwhich collects data from WeChat
- WirelessKeywhich collects wireless network information and passwords
ESET said it also identified in a remote code repository several programs written in Golang that offer reverse proxy and download functionality.
“This backdoor features a multi-step C&C protocol using DNS, as well as the ability to download and run dozens of additional Python modules with espionage capabilities,” Munoz said.
“The many components in PlushDaemon’s toolset and its rich version history show that this China-linked APT group was previously unknown, carefully developing a wide range of tools, making it a significant threat to watch out for.”