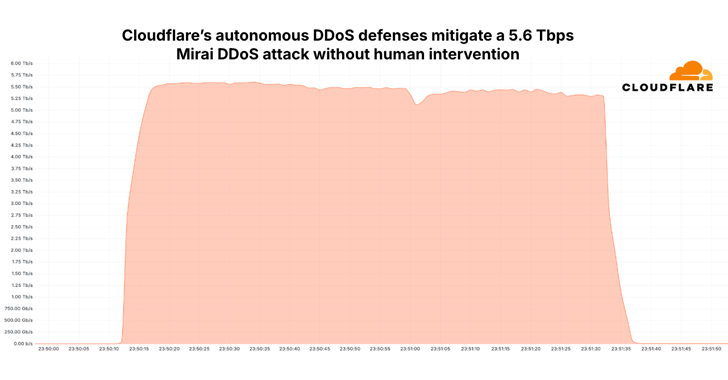
Web infrastructure and security company Cloudflare said on Tuesday that it has detected and blocked a 5.6 terabits per second (Tbps) distributed denial of service (DDoS) attack, the largest attack reported to date.
The UDP-based attack occurred on October 29, 2024. and was directed at one of the customers, an unnamed Internet Service Provider (ISP) in East Asia. The activity began with a Mirai– botnet option.
“The attack lasted just 80 seconds and occurred from more than 13,000 IoT devices,” Cloudflare’s Omer Joachimik and Jorge Pacheco. said in the report.
However, the average unique source IP observed per second was 5,500, with an average contribution of each IP per second of around 1 Gbps.
The previous record for the largest volume DDoS attack was also held informed Cloudflare in October 2024, which peaked at 3.8 Tbps.
Cloudflare also revealed that it blocked around 21.3 million DDoS attacks in 2024, a 53% increase from 2023, and that the number of attacks exceeding 1 Tbps was up 1,885% quarter-on-quarter. In the fourth quarter of 2024 alone, 6.9 million DDoS attacks were eliminated.
Some of the other notable statistics observed in Q4 2024 are listed below –
- Known DDoS botnets account for 72.6% of all HTTP DDoS attacks
- The three most common layer 3/4 (network layer) attack vectors were SYN floods (38%), DNS floods (16%) and UDP floods (14%).
- Memcached DDoS attacksBitTorrent DDoS attacks and ransom DDos attacks increased 314%, 304% and 78% quarter over quarter respectively
- About 72% of HTTP DDoS attacks and 91% of network layer DDoS attacks end in less than ten minutes
- Indonesia, Hong Kong, Singapore, Ukraine and Argentina were the biggest sources of DDoS attacks
- China, the Philippines, Taiwan, Hong Kong and Germany were the most attacked countries
- Telecommunications, internet, marketing, information technology, gambling were the most attacked sectors
The development comes courtesy of cybersecurity companies Qualys and Trend Micro revealed that offshoots of the notorious Mirai malicious botnet are targeting Internet of Things (IoT) devices, exploiting known security flaws and weak credentials to use them as a conduit for DDoS attacks.