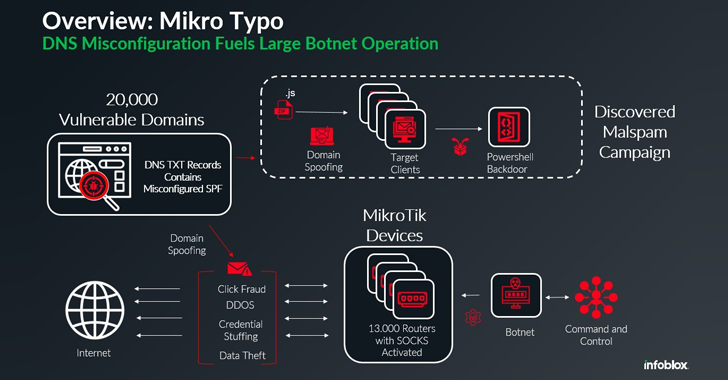
A global network of around 13,000 compromised Mikrotik routers has been used as a botnet to spread malware through spam campaigns, latest addition to a list of botnets works on MikroTik devices.
Infoblox Security Researcher David Brunsdon: The activity “takes advantage of misconfigured DNS records to communicate email protection techniques. said in a technical report published last week. “This botnet uses Mikrotik’s global network of routers to send malicious emails that appear to originate from legitimate domains.”
The DNS security company that gave the company its code name Microprinting errorsaid his analysis was based on the detection in late November 2024. of a malicious spam campaign that used invoice-related lures to trick recipients into running a ZIP archive payload.
The ZIP file contains an obfuscated JavaScript file, which is then responsible for running a PowerShell script designed to initiate an outbound connection to the management server (C2) located at IP address 62.133.60(.)137.
The exact initial access vector used to infiltrate the router is unknown, but various firmware versions were affected, including those vulnerable to CVE-2023-30799a critical elevation of privilege issue that can be abused to execute arbitrary code.
“Regardless of how they were compromised, it appears that the actor placed a script on the (Mikrotik) devices that includes SOCKS (Secure Sockets), which allow the devices to act as TCP redirectors,” Brunsdon said.
“Enabling SOCKS effectively turns each device into a proxy server, masking the true origin of malicious traffic and making it difficult to trace back to its source.”
Adding to the concern is the lack of authentication required to use these proxies, allowing other threat actors to use specific devices or the entire botnet for malicious purposes ranging from distributed denial of service (DDoS) attacks to phishing campaigns.
The spam company in question was found to be using a misconfiguration as part of the sender’s policy (SPF) TXT records of 20,000 domains, giving attackers the ability to send emails on behalf of those domains and bypass various email protection tools.
In particular, SPF entries were found to be configured with the extremely permissive “+all” option, which essentially defeats the purpose of the protection. This also means that any device, such as compromised MikroTik routers, can spoof a legitimate domain in an email.
MikroTik device owners are advised to constantly update their routers and change their default credentials to prevent any exploit attempts.
“With so many MikroTik devices compromised, the botnet is capable of launching a wide range of malicious activities, from DDoS attacks to data theft and phishing campaigns,” Brunsdon said. “The use of SOCKS4 proxies further complicates detection and mitigation efforts, highlighting the need for robust security measures.”