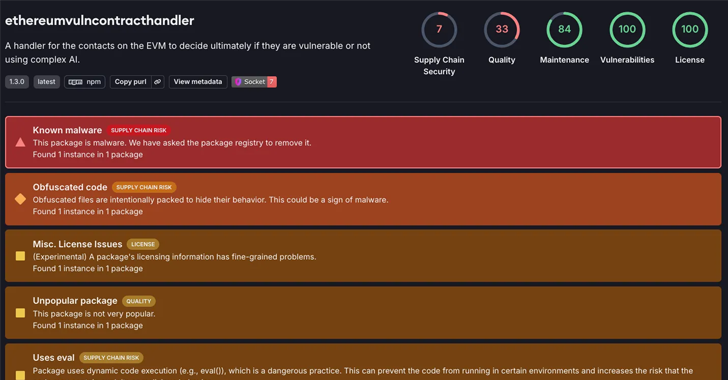
Cybersecurity researchers discovered a malicious package in the npm package registry that pretends to be a library for detecting vulnerabilities in Ethereum smart contracts, but actually drops an open-source remote access trojan called Quasar RAT onto developer systems.
A highly confusing package called ethereumvulncontracthandlerwas published to npm on Dec 18, 2024. by a user named “solidit-dev-416”. At the time of writing, it is still available for download. It was downloaded 66 times to date.
“Once installed, it retrieves a malicious script from a remote server, executing it silently to deploy the RAT on Windows systems,” Socket security researcher Kirill Boichenko said in an analysis published last month.
The malicious code embedded in the ethereumvulncontracthandler is hidden with multiple layers of obfuscation using techniques such as Base64 and XOR encoding, as well as minification to resist analysis and detection attempts.
The malware also performs checks to avoid sandboxing before impersonating a bootloader, retrieving and executing the second-stage payload from a remote server (“jujuju(.)lat”). The script is designed to run PowerShell commands to initiate Quasar RAT execution.
The Remote Access Trojan, for its part, establishes security through modifications to the Windows registry and contacts the Command and Control (C2) server (“captchacdn(.)com:7000”) to receive further instructions that allow it to collect and steal information. .
Quasar RAT, the first publicly released on GitHub in July 2014, was used for both cybercrime and cyber espionage companies by various threat actors over the years.
“The threat actor also uses this C2 server to catalog infected machines and manage multiple compromised nodes at the same time if that company is part of a botnet infection,” Boychanka said.
“At this stage, the victim’s machine is fully compromised and under full surveillance and control by the threat actor, ready to regularly log in and receive updated instructions.”
The issue of fake stars on GitHub
A new study by Socket, along with researchers at Carnegie Mellon University and North Carolina State University, has found a rapid spike in the number of fake “stars” being used to artificially boost the popularity of GitHub repositories with malware.
While phenomenon was around for a whileresearch has shown that most fake stars are used to promote short-lived malware repositories masquerading as pirated software, game codes, and cryptocurrency bots.
Promoted through GitHub star traders such as Baddhi Shop, BuyGitHub, FollowDeh, R for Rank and Twidium, the “open” black market is believed to be behind 4.5 million “fake” stars from 1.32 million accounts and spans 22,915 storage, which illustrates the scale of the problem.
Baddhi ShopHacker news foundallows potential customers to buy 1,000 GitHub stars for $110. “Buy followers, stars, forks, and followers on GitHub to increase the authority and visibility of your repository,” the site’s description reads. “Real engagement attracts more developers and contributors to your project!”
“Only a few repositories with fake star companies are published in package registries such as npm and PyPI,” the researchers note. said. “Widely accepted even less. At least 60% of accounts involved in fake star campaigns have trivial activity patterns.”
As the open source software supply chain continues to be an attractive vector for cyberattacks, the results confirm that the number of stars alone is an unreliable signal of quality or reputation and should not be used without further verification.
In a statement provided to WIRED in October 2023, the Microsoft-owned code hosting platform said it has known about the problem for years and is actively working to remove fake stars from the service.
“The main vulnerability of the star count as a metric is that the actions of all GitHub users are weighted equally in its determination,” the researchers said.
“As a result, as we have shown in our research, the number of stars can easily be inflated by a large number of bot accounts or (perhaps with low reputation) crowdsourced people. To avoid such exploitation, GitHub may consider providing a weighted metric for the signal repository. popularity (e.g. based on measures of network centrality) that are much harder to fake.”