A new phishing campaign has been spotted using tax-themed lures to deliver hidden backdoor payloads in attacks against Pakistan.
Cybersecurity company Securonix, which tracks activity under the name FLUX#CONSOLEsaid it most likely starts with a phishing link to an email or attachment, although it said it could not obtain the original email used to launch the attack.
“One of the most notable aspects of the campaign is how threat actors use Microsoft Common Console Document (MSC) files to deploy a bootloader and dual-purpose bootloader to deliver further malicious payloads,” security researchers Dan Yuzwick and Tim Peck said.
It should be noted that the abuse of specially crafted saved Management Console (MSC) files to execute malicious code has been codenamed GrimResource by Elastic Security Labs.
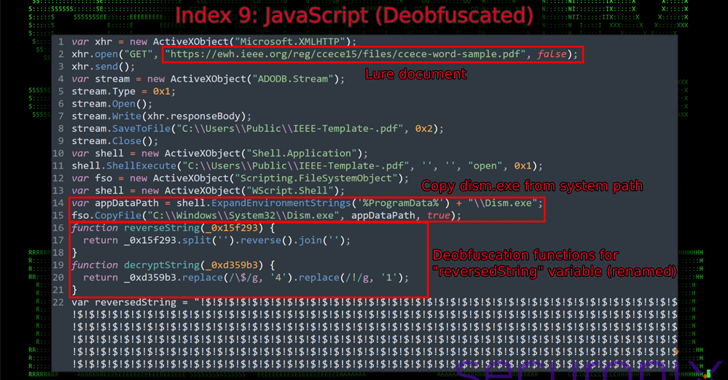
The starting point is a double-extension file (.pdf.msc) that masquerades as a PDF file (when the setting to display file extensions is disabled) and is designed to execute embedded JavaScript code when launched using the Microsoft Management Console (MMC). ).
This code, in turn, is responsible for receiving and displaying the decoy file, as well as stealthily loading a DLL file (“DismCore.dll”) in the background. One such document used in the campaign is called “Tax Reductions, Rebates and Credits 2024” which is a legal document related to Pakistan Federal Board of Revenue (FBR).
“In addition to delivering the payload from an embedded and obfuscated string, the .MSC file is able to execute additional code by accessing a remote HTML file, which also achieves the same goal,” the researchers said, adding that persistence is established using a scheduled task.
The main payload is a backdoor capable of contacting a remote server and executing commands sent to it to steal data from compromised systems. Securonix said the attack was stopped 24 hours after the initial infection.
“From the highly obfuscated JavaScript used in the initial stages to the deeply hidden malware code in DLLs, the entire chain of attacks illustrates the complexity of detecting and analyzing modern malware,” the researchers said.
“Another notable aspect of this campaign is the use of MSC files as a potential evolution of the classic LNK file that has been popular with threat actors over the past few years. Like LNK files, they also allow malicious code to be executed during mashup. into legitimate Windows administrative workflows.”