Cybersecurity researchers have shed light on a previously undocumented aspect of ClickFix-style attacks that involve taking advantage of a single ad network service in an ad-driven phishing campaign. Cheat ads.
“This campaign, based entirely on a single ad network for distribution, demonstrates the basic mechanisms of malicious advertising – delivering over 1 million daily ‘ad impressions’ (over the last ten days) and causing thousands of daily victims to lose their accounts and money through a network of 3,000 + content sites that drive traffic” – Nati Tal, Head of Guardio Labs, said in a report shared with The Hacker News.
Hiking, like documented by several cybersecurity companies in recent months, include directing visitors to pirated movie sites and others to fake CAPTCHA pages that tell them to copy and execute a Base64-encoded PowerShell command, ultimately leading to the deployment of information stealers like Lumma.
With Proofpoint, attacks are no longer limited to one actor recently stating that several unattributed threat clusters have used a clever social engineering approach to deliver remote access trojans, stealers, and even post-exploitation frameworks like Brute Ratel C4.
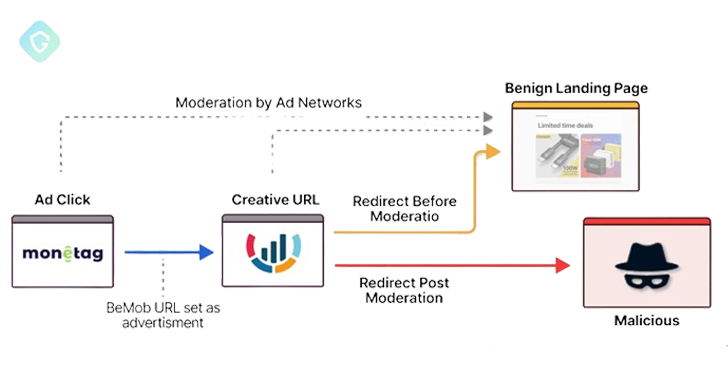
Guardio Labs said it was able to trace the company’s origins to Monetag, a platform that claims to offer multiple ad formats for “website monetization, social traffic, Telegram mini-apps,” with threat actors also using services such as ad tracking BeMob to hide their evil intentions. Monetag is also tracked by Infoblox under the names Vane Viper and Omnatuor.
In fact, the campaign boils down to the following: website owners (i.e. threat actors) register with Monetag, after which the traffic is redirected to a traffic distribution system (TDS), which is operated by a malicious ad network, and ultimately leads visitors to a CAPTCHA verification page.
“By feeding a good BeMob URL to Monetag’s ad management system instead of a straight fake captcha page, the attackers took advantage of BeMob’s reputation, complicating Monetag’s content moderation efforts,” Tal explained. “This TDS BeMob finally redirects to a malicious CAPTCHA page hosted on services like Oracle Cloud, Scaleway, Bunny CDN, EXOScale, and even Cloudflare’s R2.”
After responsible disclosure, Monetag removed more than 200 accounts associated with the threat. BeMob similarly removed accounts used for cloaking. However, there are signs that the company has recovered on December 5, 2024.
The findings reiterate the need for content moderation and robust account verification to prevent fraudulent registrations.
“From fraudulent publisher sites that offer pirated content or content bait, to sophisticated redirect chains and cloaking techniques, this campaign highlights how ad networks created for legitimate purposes can be weapons for malicious activity,” Tal said.
“The result is a disjointed chain of responsibility in which ad networks, publishers, ad statistics services and hosting providers play a role, but often avoid responsibility.”