A threat actor known as Hammeredon the use of leverage was observed Cloudflare Tunnels as a tactic to hide its staging infrastructure, which hosts a malware called GammaDrop.
The activity is part of the constant phishing campaign In a new analysis, Recorded Future’s Insikt Group said it has targeted Ukrainian organizations since at least early 2024 and is designed to eliminate Visual Basic Script malware.
The cybersecurity company is tracking the threat under the name BlueAlpha, which is also known as Aqua Blizzard, Armageddon, Hive0051, Iron Tilden, Primitive Bear, Shuckworm, Trident Ursa, UAC-0010, UNC530 and Winterflounder. A group believed to be active since 2014 affiliated with the Federal Security Service of Russia (FSB).
“BlueAlpha recently started using Cloudflare Tunnels to hide the intermediate infrastructure in use GammaDropan increasingly popular method used by cybercriminal groups to deploy malware,” Insikt Group noted.
“BlueAlpha continues to use the Domain Name System (DNS) fast flowing GammaLoad (C2) command and control infrastructure to make it more difficult to track and disrupt C2 communications to maintain access to compromised systems.”
The adversary’s use of Cloudflare Tunnel was previously documented by Slovak cyber security company ESET in September 2024 as part of attacks on Ukraine and various NATO countries, namely Bulgaria, Latvia, Lithuania and Poland.
He also described the threat actor’s skill as reckless and not particularly focused on stealth, even though they make every effort to “avoid being locked down by security products and try very hard to maintain access to compromised systems.”
“Gamaredon attempts to maintain its access by simultaneously deploying multiple simple bootloaders or backdoors,” ESET added. “The lack of sophistication of Gamaredon’s tools is compensated by frequent updates and the use of obfuscation that changes regularly.”
The tools are primarily designed to steal valuable data from web applications running in Internet browsers, email clients, and instant messaging programs such as Signal and Telegram, as well as to download additional payloads and distribute malware via connected USB drives. .
- PteroPSLoad, PteroX, PteroSand, PteroDash, PteroRisk and PteroPowder – payload loading
- PteroCDrop – Dropping Visual Basic Script payloads
- PteroClone – Delivering payloads using the rclone utility
- PteroLNK – Arming connected USB drives
- PteroDig – Weaponize LNK files in desktop folder for saving
- PteroSocks – Provides partial SOCKS proxy functionality
- PteroPShell, ReVBShell – functions as a remote shell
- PteroPSDoor, PteroVDoor – Exfiltration of specific files from the file system
- PteroScreen – Capture and extract screenshots
- PteroSteal – Exfiltrate credentials stored by web browsers
- PteroCookie – Exfiltration of cookies stored by web browsers
- PteroSig – Exfiltrate data stored by the Signal application
- PteroGram – Exfiltrate data stored in the Telegram application
- PteroBleed – Exfiltrate data saved by Telegram and WhatsApp web versions from Google Chrome, Microsoft Edge and Opera
- PteroScout – Exfiltration of system information
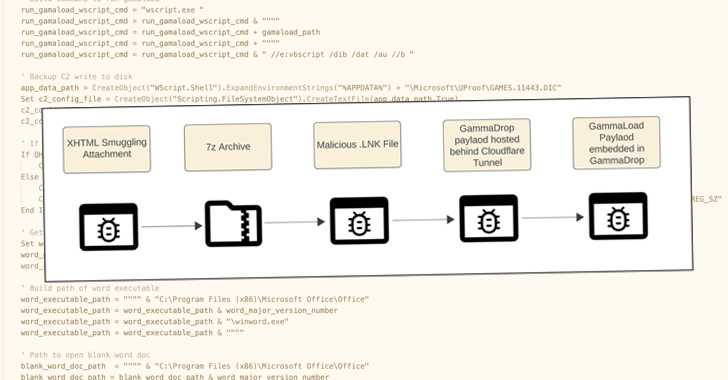
The latest series of attacks covered by Recorded Future involves sending phishing emails with HTML attachments that use a technique called HTML smuggling to activate the infection process via embedded JavaScript code.
When opened, the HTML attachments drop a 7-Zip archive (“56-27-11875.rar”) containing a malicious LNK file that uses mshta.exe to deliver GammaDrop, an HTA program responsible for writing to disk a custom bootloader named GammaLoad, which then contacts the C2 server to receive additional malware.
The GammaDrop artifact is extracted from a proxy server behind a Cloudflare tunnel located at the amsterdam-sheet-veteran-aka.trycloudflare(.)com domain.
For its part, GammaLoad uses DNS-over-HTTPS (DoH) providers such as Google and Cloudflare to resolve C2 infrastructure when traditional DNS fails. It also uses the fast DNS flow technique to obtain the C2 address if the first attempt to contact the server fails.
“BlueAlpha will likely continue to improve its evasion techniques using widely used legitimate services such as Cloudflare, making detection difficult for traditional security systems,” Recorded Future said.
“Continued improvements in HTML smuggling and DNS-based security are likely to create new challenges, especially for organizations with limited threat detection capabilities.”