A popular open source game engine called Godot Engine is being misused as part of a new GodLoader malware campaign, infecting more than 17,000 systems since at least June 2024.
“Cybercriminals used the Godot Engine to execute crafted GDScript code that runs malicious commands and delivers malware,” Check Point reported. said in a new analysis published Wednesday. “The method remains undetected by almost all antivirus engines on VirusTotal.”
It’s no surprise that threat actors are constantly looking for new tools and techniques that can help them deliver malware, bypassing security detection, even as defenders continue to erect new fences.
Latest addition Godot enginea game development platform that allows users to create 2D and 3D games on different platformsincluding Windows, macOS, Linux, Android, iOS, PlayStation, Xbox, Nintendo Switch and the Internet.
Multi-platform support also makes it an attractive tool in the hands of adversaries, who can now use it to target and infect devices at scale, effectively expanding the attack surface.
A company stands out because of what it uses Stargazers Ghost Network – in this case, a set of around 200 GitHub repositories and over 225 fake accounts – as a distribution vector for GodLoader.
“These accounts were the main actors of the malicious repositories that distribute GodLoader, making them appear legitimate and safe,” Check Point said. “The vaults were released in four separate waves, mainly targeting developers, gamers, and casual users.”
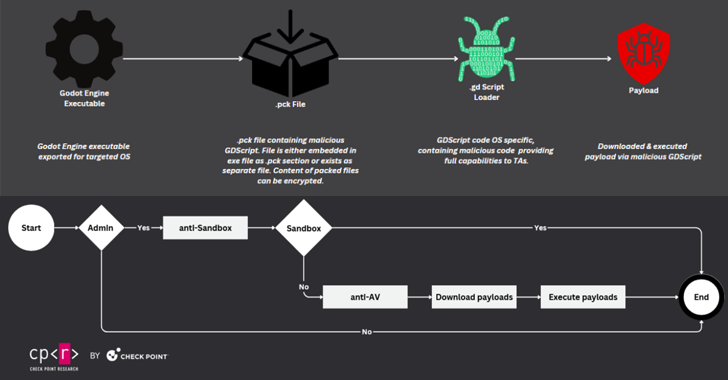
Attacks observed on September 12, September 14, September 29, and October 3, 2024 were found to use Godot Engine executables, also known as pack (or .PCK) files, to remove bootloader malware, which is then responsible for to download and execute end-stage payloads such as RedLine Stealer and XMRig cryptocurrency miner from Bitbucket repository.
Additionally, the bootloader includes features to bypass sandbox and virtual environment scanning and add the entire C:\ drive to Microsoft Defender Antivirus list of exceptions to prevent detection of malware.
The cybersecurity company said the GodLoader artifacts primarily target Windows machines, although it noted that it is easy to adapt them to infect macOS and Linux systems.
Moreover, while the current set of attacks involves threat actors creating custom Godot Engine executables to spread malware, they could be taken a notch higher by spoofing a legitimate game built by Godot once obtained symmetric encryption key is used to extract the .PCK file.
This kind of attack, however, can be prevented by switching to an asymmetric key algorithm (aka public key cryptography), which relies on a pair of public and private keys to encrypt/decrypt data.
The malicious campaign serves as yet another reminder of how threat actors often use legitimate services and brands to evade security mechanisms that require users to download software only from trusted sources.
“Threat actors have exploited Godot scripting capabilities to create custom bootloaders that remain undetected by many conventional security solutions,” Check Point said. “Because Godot’s architecture allows for cross-platform payload delivery, attackers can easily deploy malicious code on Windows, Linux, and macOS, sometimes even exploring Android variants.”
“The combination of a targeted distribution method and a discreet, undetected technique has resulted in exceptionally high levels of infection. This cross-platform approach increases the versatility of malware, giving threat actors a powerful tool that can easily target multiple operating systems. This method allows attackers to deliver malware more efficiently across multiple devices, increasing their reach and impact.”