Cybersecurity researchers have uncovered two new attack techniques against infrastructure-as-code (IaC) and policy-as-code (PaC) tools such as Terraform and HashiCorp’s Open Policy Agent (OPA) that use special domain-oriented languages (DSLs) to hack cloud platforms and extracted data.
“Because they’re hard languages with limited capabilities, they should be more secure than standard programming languages, and they really are,” Tenable Senior Security Researcher Shelly Raban said in a technical report published last week. “However, safer does not mean bulletproof.”
OPA is a popular open-source policy engine that allows organizations to enforce policies on their own cloud environments, such as microservices, CI/CD pipelines, and Kubernetes. Policies are defined using the native query language called Rega which then evaluated under OPA to return the decision.
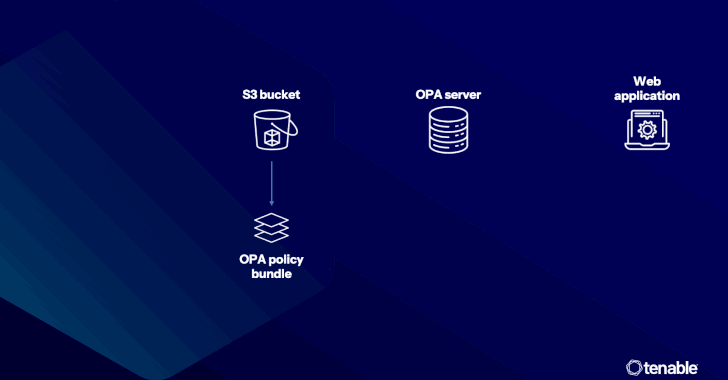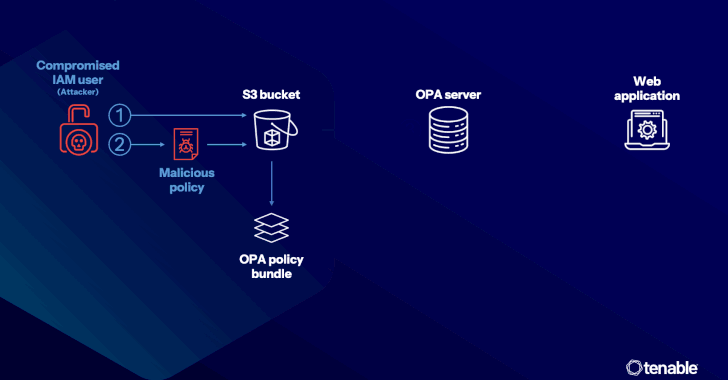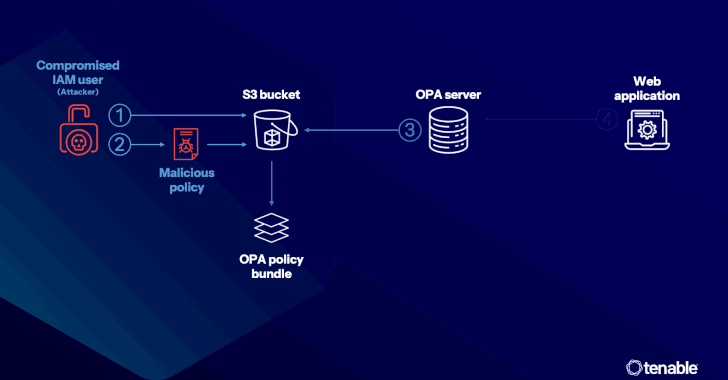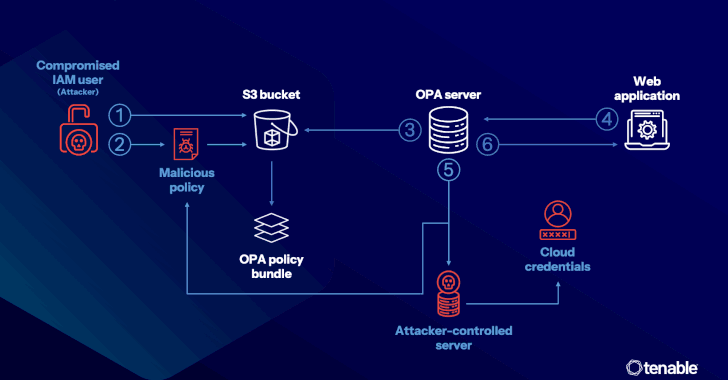
The attack method developed by Tenable targets the supply chain, where an attacker gains unauthorized access via a compromised access key to inject a malicious Rego policy into the OPA server, which is then used in the policy decision stage to allow malicious activities such as credential theft data using a built-in function known as “http.send.”
Even in cases where OPA deployments restrict the use of http.send, the cybersecurity firm discovered that another feature called “net.lookup_ip_addr” to smuggle data using DNS lookups using a technique called DNS tunneling.
“So the net.lookup_ip_addr function is another function that you might want to limit or at least pay attention to in policy as it also creates a risk of data theft from your OPA deployment,” Raban said.
Terraform, similar to OPA, goals to simplify the process of configuring, deploying, and managing cloud resources using code-based definitions. These configurations can be configured using another declarative DSL called HashiCorp Configuration Language (HCL).
An attacker can target an open source IaC platform by exploiting its “terraform plan” commands that are usually run as part of GitHub “pull_query” workflows to commit unverified changes containing the malicious data source during the CI/CD process.
“This poses a risk as an external attacker in a public repository or a malicious insider (or an external attacker with leverage) in a private repository could exploit the pull request for their own malicious purposes,” Tenable noted. “The data sources run during the ‘terraforming plan’, which greatly reduces the entry point for attackers.”
These data sources, in turn, can be a fake external data source, a Terraform module, or a DNS data sourcewhich requires the use of only third-party components from trusted sources. Some of the other recommendations to reduce such risks include:
- Implement granular role-based access control (RBAC) and adhere to the principle of least privilege
- Configure application-level and cloud-level logging for monitoring and analysis
- Restrict network and data access to applications and host machines
- Prevent automatic execution of untested and potentially malicious code in CI/CD pipelines
In addition, organizations can use IaC scanning tools and solutions like Terrascan and Checkov to proactively detect misconfigurations and compliance issues before deployment.