Threat actors have been found to be using a new technique that abuses macOS extended file attributes to smuggle a new malware called RustyAttr.
A Singaporean cyber security company has attributed to new activity with moderate credibility for the notorious North Korea-linked Lazarus Group, citing infrastructural and tactical overlaps seen with previous campaigns, including RustBucket.
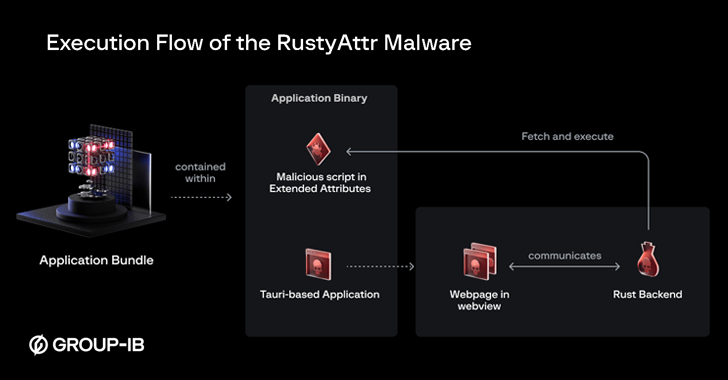
Extended attributes refer to additional metadata associated with files and directories that can be extracted using a special command called xattr. They are often used to store information beyond standard attributes such as file size, timestamps, and permissions.
The malware detected by Group-IB is created using Difficultiescross-platform framework for desktop applications, and signed by a leaked certificate that has since been revoked by Apple. They include an extended attribute that is configured to retrieve and run a shell script.
Executing the shell script also triggers a decoy that serves as a distraction mechanism by displaying a “This app doesn’t support this version” error message or a seemingly innocuous PDF document related to the development and funding of game projects.
“Once the application is executed, Tauri tries to render the HTML web page using WebView,” said Sharmin Lowe, Group-IB security researcher. “(The threat actor) used some random pattern taken from the Internet.”
But it’s also worth noting that these web pages are designed to load malicious JavaScript, which then fetches the content of the extended attributes and executes it using the Rust backend. However, the spoofed web page ends up being rendered only in cases where there are no extended attributes.
The ultimate purpose of the campaign remains unclear, especially in light of the fact that there was no evidence of further payloads or confirmed casualties.
“Fortunately, macOS systems provide some level of protection for found samples,” Lowe said. “To trigger an attack, users must disable Gatekeeper by disabling malware protection. It is likely that some degree of engagement and social engineering will be required to convince victims to take these steps.”
The development is the same as the North Korean threat actors attraction Art broad companies who strive safe remote positions with companies around the world, as well as tricking current employees working at cryptocurrency companies into downloading malware under the guise of a coding interview.