A security analysis of cloud platform OvrC found 10 vulnerabilities that could be linked to allow potential attackers to remotely execute code on connected devices.
“Attackers who successfully exploit these vulnerabilities could gain access, control, and compromise OvrC-enabled devices; some of which include smart power supplies, cameras, routers, home automation systems, and more,” Uri Katz, researcher at Claroty. said in the technical report.
Snap One’s OvrC, pronounced “oversee,” is touted as a “revolutionary support platform” that allows homeowners and businesses to remotely manage, configure, and troubleshoot IoT devices on their network. According to its website, OvrC solutions are deployed in more than 500,000 end-user locations.
According to A coordinated advisory issued by the US Cybersecurity and Infrastructure Security Agency (CISA), successful exploitation of the identified vulnerabilities could allow an attacker to “impersonate and claim devices, execute arbitrary code, and reveal information about an affected device.”
The flaws were found to affect OvrC Pro and OvrC Connect, and the company released fixes for eight of them in May 2023 and the remaining two on November 12, 2024.
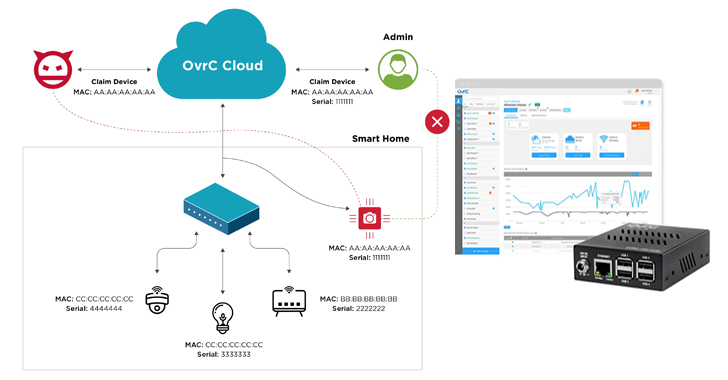
“Many of these issues we’ve found are caused by ignoring the device’s interface to the cloud,” Katz said. “In many of these cases, the underlying problem is the potential for cross-claims against IoT devices due to weak identifiers or similar errors. These issues range from weak access controls, authentication bypass, failed input validation, hard-coded credentials, and remote code execution flaws. .”
As a result, a remote attacker could abuse these vulnerabilities to bypass the firewall and gain unauthorized access to the cloud management interface. Even worse, access can be used to enumerate and profile devices, hijack devices, elevate privileges, and even run arbitrary code.
The most serious disadvantages are listed below –
- CVE-2023-28649 (CVSS v4 score: 9.2), which allows an attacker to impersonate the hub and hijack the device
- CVE-2023-31241 (CVSS v4 score: 9.2) which allows an attacker to claim arbitrary unsolicited devices by bypassing the serial number requirement
- CVE-2023-28386 (CVSS v4 score: 9.2) which allows an attacker to download arbitrary firmware updates leading to code execution
- CVE-2024-50381 (CVSS Score v4: 9.1), which allows an attacker to impersonate a hub and arbitrarily give up devices, then use other vulnerabilities to take control of them
“With more devices coming online every day and cloud management becoming the dominant means of configuring and accessing services, it’s more important than ever for manufacturers and cloud service providers to protect these devices and connections,” said Cat. “Negative results could affect connected power supplies, business routers, home automation systems and more connected to the OvrC cloud.”
Disclosure is as Nozomi Networks in detail three security flaws affecting EmbedThis Forwarda compact web server used in embedded and IoT devices that can lead to a denial of service (DoS) under certain conditions. The vulnerabilities (CVE-2024-3184, CVE-2024-3186, and CVE-2024-3187) were fixed in GoAhead version 6.0.1.
There have also been many security flaws in recent months uncovered in Johnson Controls’ exacqVision web service, which can be combined to take control of video streams from surveillance cameras connected to the application and steal credentials.