Cybersecurity researchers have discovered new security flaws affecting Citrix virtual applications and desktops that could be exploited for unauthenticated remote code execution (RCE).
Release, according to the findings of observation towerrooted in Art Session recording a component that allows system administrators to capture user activity and record keyboard and mouse input along with a desktop video stream for auditing, compliance, and troubleshooting.
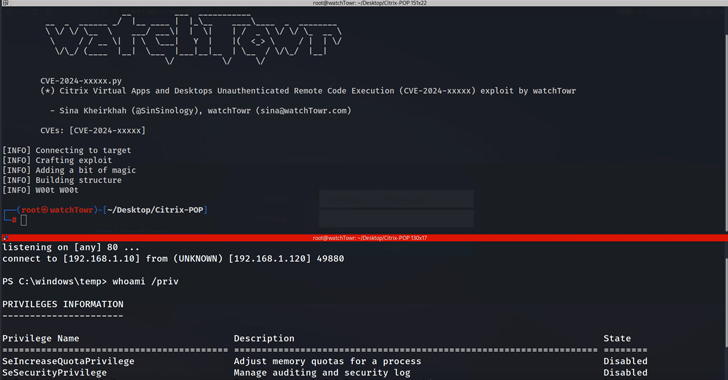
Specifically, the vulnerability exploits “a combination of carelessly exposed MSMQ an instance with misconfigured permissions that uses BinaryFormatter can be accessed from any host over HTTP to perform RCE without authentication,” said security researcher Sina Heirkha.
The vulnerability details listed below –
- CVE-2024-8068 (CVSS Score: 5.1) – Elevate access privileges to the NetworkService account
- CVE-2024-8069 (CVSS Score: 5.1) – Limited remote code execution with NetworkService account privilege
However, Citrix noted that for successful exploitation, an attacker must be an authenticated user in the same Windows Active Directory domain as the session recording server’s domain and on the same internal network as the session recording server. The bugs have been fixed in the following versions –
- Citrix Virtual Apps and Desktops before patch 2407 24.5.200.8
- Citrix Virtual Apps and Desktops 1912 LTSR to CU9 patch 19.12.9100.6
- Citrix Virtual Apps and Desktops 2203 LTSR to patch CU5 03/22/5100.11
- Citrix Virtual Apps and Desktops 2402 LTSR to patch CU1 02/24/1200.16
It should be noted that Microsoft has urged developers should stop using BinaryFormatter for deserialization because the method is unsafe when used with untrusted input. The BinaryFormatter implementation was removed with .NET 9 as of August 2024.
“BinaryFormatter was implemented before deserialization vulnerabilities became a well-known threat category,” the tech giant said notes in its documentation. “As a result, the code is not in line with current best practice. BinaryFormatter.Deserialize may be vulnerable to other categories of attacks, such as information disclosure or remote code execution.”
At the heart of the problem is the Session Recording Storage Manager, a Windows service that manages the recorded session files received from each computer that has this feature enabled.
While Storage Manager receives session records as message bytes through the Microsoft Message Queuing (MSMQ) service, the analysis found that a serialization process is used to transfer the data and that the queue instance has excessive privileges.
Worse, the data received from the queue is deserialized using the BinaryFormatter, allowing an attacker to abuse unsafe permissions set during the initialization process to pass specially crafted MSMQ messages sent over HTTP through the internet.
“We know there is an instance of MSMQ with misconfigured permissions, and we know it uses the infamous BinaryFormatter class to perform deserialization,” Heirkha said, detailing the steps involved in creating the exploit. “The cherry on top is that it can be reached not only locally, via MSMQ’s TCP port, but also from any other host, via HTTP.”
“This combination allows for good old unauthenticated RCE,” the researcher added.