The Russian threat known as RomCom has been linked to a new wave of cyberattacks targeting Ukrainian government agencies and unidentified Polish organizations since at least late 2023.
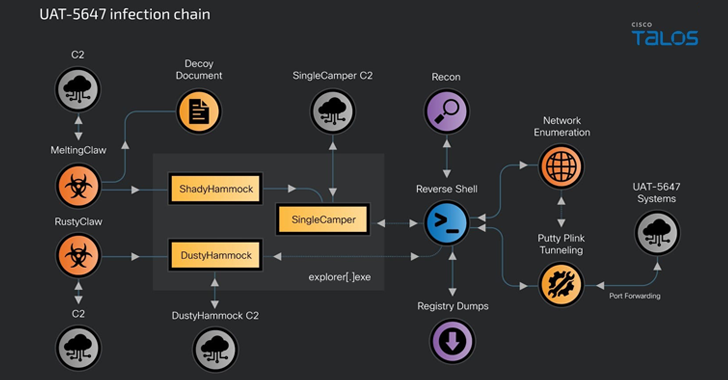
Intrusions are characterized by the use of a variety of Art RAT RomCom called SingleCamper (aka SnipBot or RomCom 5.0), reported Cisco Talos, which monitors a cluster of activity under the alias UAT-5647.
“This version loads directly from the registry into memory and uses a loopback address to communicate with its loader,” security researchers Dmitry Karzhevin, Ashir Malhotra, Vanya Sveitzer, and Vitor Ventura noted.
Also tracked as Storm-0978, Tropical Scorpius, UAC-0180, UNC2596, and Void Rabisu, RomCom has been involved in various motivational operations such as ransomware, extortion, and targeted credential harvesting since its appearance in 2022.
It has been estimated that the operational pace of their attacks has increased in recent months with the aim of establishing long-term storage of compromised networks and stealing data, which suggests clear espionage.
To that end, the threat creator is allegedly “aggressively expanding its tools and infrastructure to support a wide range of malware components built in different languages and platforms,” such as C++ (ShadyHammock), Rust (DustyHammock), Go (CLUEGG), and Lua (A DROP).
The attack chains start with a phishing message delivered by a loader coded in C++ (MeltingClaw) or Rust (RustyClaw) that serves to deploy the ShadyHammock and DustyHammock backdoors, respectively. At the same time, a decoy document is shown to the recipient to maintain the ruse.
While the DustyHammock is designed to communicate with the control server (C2), execute arbitrary commands, and download files from the server, the ShadyHammock acts as a launch pad for the SingleCamper and also listens for incoming commands.
Despite ShadyHammock’s additional features, it is believed to be the predecessor of DustyHammock, given the fact that attacks on the latter were seen as recently as September 2024.
SingleCamper, the latest version of the RomCom RAT, is responsible for a wide range of post-hacking activities that involve downloading PuTTY’s Plink tool to create remote tunnels with enemy-controlled infrastructure, network reconnaissance, lateral movement, user and system detection, and data theft.
“This particular series of attacks targeting high-ranking Ukrainian organizations is likely designed to fulfill UAT-5647’s two-pronged strategy in stages—establish long-term access and steal data for as long as possible to further espionage motives, then potentially turn to deploying ransomware to disrupt and likely benefit financially from the compromise,” the researchers said.
“It is also likely that Polish organizations were also targeted, based on keyboard language checks performed by the malware.”