Cybersecurity researchers have uncovered a new malware campaign that delivers Hijack Loader artifacts signed with legitimate code signing certificates.
French cybersecurity firm HarfangLab, which discovered the activity earlier this month, said chain attacks aimed at deploying an information stealer known as Lumma.
Hijack bootloaderalso known as DOILoader, IDAT Loader and SHADOWLADDER, first appeared in September 2023. Malware loader attack chains usually involve forcing users to download a binary file disguised as pirated software or movies.
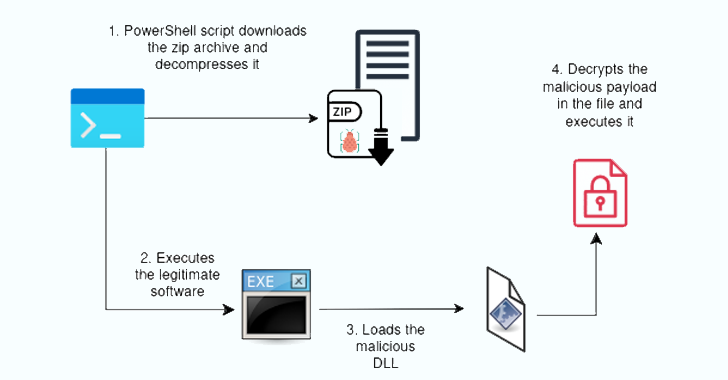
Recent variations of these companies have been found to direct users to fake CAPTCHA pages that prompt site visitors to prove they are human by copying and executing a coded PowerShell command that extracts the malicious payload in the form of a ZIP archive.
HarfangLab said it observed three different versions of the PowerShell script starting in mid-September 2024 –
- A PowerShell script that uses mshta.exe to execute code hosted on a remote server
- A remotely hosted PowerShell script that is directly executed via the The Invoke-Expression cmdlet (aka what)
- A PowerShell script that uses msiexec.exe to download and execute a payload from a remote URL
A ZIP archive, on the other hand, contains a real executable file that can be side-loaded by a DLL, and a malicious DLL (such as a Hijack Loader) that must be loaded instead.
“The purpose of the HijackLoader sideloader DLL is to decrypt and execute the encrypted file contained in the package,” HarfangLab said. “This file hides the final stage of HijackLoader, which aims to download and execute the hijacking implant.”
The delivery mechanism is said to have been changed from sideloading DLLs to using multiple signed binaries in early October 2024 in an attempt to avoid detection by security software.
It is currently unclear whether all of the code-signing certificates were stolen or intentionally created by the threat actors themselves, although the cybersecurity firm assessed with low to medium confidence that it could be the latter. The certificates have since been revoked.
“We have noticed that for several CAs that issue certificates, obtaining and activating a code signing certificate is largely automated and only requires a valid company registration number and a contact person,” it said. “This study highlights that malware can be signed, emphasizing that code signing alone cannot serve as a baseline measure of trustworthiness.”
The development comes after SonicWall Capture Labs warned of a surge in cyberattacks infecting Windows machines with malware called CoreWarrior.
“This is a persistent Trojan that tries to spread rapidly by creating dozens of copies of itself and addressing multiple IP addresses, opening multiple sockets for backdoor access, and plugging in Windows UI elements for monitoring,” the report said. said.
Phishing campaigns have also been observed delivering product and bootloader malware known as XWorm using a Windows Script File (WSF), which in turn loads and executes a PowerShell script located on paste(.)ee.
The PowerShell script then runs a Visual Basic script that acts as a conduit to execute a series of batch and PowerShell scripts to load the malicious DLL responsible for injecting XWorm into a legitimate process (“RegSvcs.exe”).
The latest version of XWorm (version 5.6) includes the ability to report response times, collect screenshots, read and modify the victim’s hosts file, perform a denial-of-service (DoS) attack against the target, and remove stored plugins, indicating an attempt to avoid leaving a forensic trail.
“XWorm is a multi-faceted tool that can provide an attacker with a wide range of capabilities,” Ian Michael Alcantara, security researcher at Netskope Threat Labs. said.