The Iranian threat actor known as Oil rig A patched privilege escalation flaw affecting the Windows kernel was seen being used in a cyber espionage campaign targeting the UAE and the wider Gulf region.
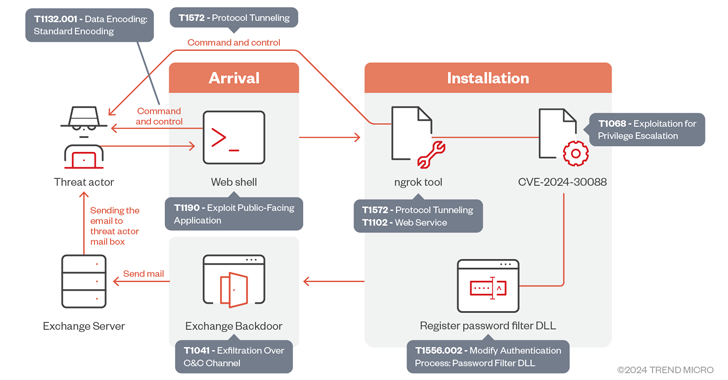
“The group uses sophisticated tactics that include deploying a backdoor that uses Microsoft Exchange servers to steal credentials and exploiting vulnerabilities such as CVE-2024-30088 for elevation of privilege,” Trend Micro researchers Mohamed Fahmi, Bahaa Yamani, Ahmed Kamal and Nick Dye said in an analysis published on Friday.
A cyber security company tracks down a pseudonymous threat actor The land of Simnavazwhich is also called APT34, Crambus, Cobalt Gypsy, GreenBug, Hazel Sandstorm (formerly EUROPIUM), and Helix Kitten.
The chain of attacks involves the deployment of a previously undocumented implant that comes with the ability to steal credentials via on-premises Microsoft Exchange servers, a proven tactic adopted by adversaries in the past, while also incorporating newly discovered vulnerabilities into its arsenal of exploits.
CVE-2024-30088, patched up Microsoft in June 2024 addresses a privilege escalation case in the Windows kernel that can be used to gain SYSTEM privileges, assuming attackers can win the race.
Initial access to target networks is facilitated by infiltrating a vulnerable web server to remove the web shell, followed by uninstalling the ngrok remote management tool to maintain persistence and moving to other network endpoints.
The elevation of privilege vulnerability then serves as a delivery channel for a backdoor codenamed STEALHOOK responsible for sending harvested data via an Exchange server to an attacker-controlled email address as an attachment.
A notable technique used by OilRig in the latest set of attacks involves abusing elevated privileges to deny password filter Policy DLL (psgfilter.dll) to retrieve sensitive credentials from domain users through domain controllers or local accounts on local machines.
“The attacker was very careful with exposed passwords when implementing password filter export features,” the researchers said. “The threat actor also used clear text passwords to gain access and remotely deploy the tools. Plaintext passwords were first encrypted before being stolen when sent over the network.”
It should be noted that the use of psgfilter.dll was observed back in December 2022 in connection with a campaign targeting organizations in the Middle East using another backdoor called MrPerfectionManager.
“Their recent activity suggests that Earth Simnavaz is focused on exploiting vulnerabilities in key infrastructure in geopolitically sensitive regions,” the researchers noted. “They also seek to gain a foothold in compromised facilities so they can use the weapon to attack additional targets.”