Cybersecurity researchers discovered a malicious Android app in the Google Play Store that allowed threat actors to steal approximately $70,000 in cryptocurrency from victims over a period of nearly five months.
The malicious program identified by Check Point appeared to be legitimate WalletConnect open source protocol to force unsuspecting users to download it.
“Fake reviews and consistent branding have helped the app get over 10,000 downloads, ranking high in search results,” the cybersecurity firm said. said in the analysis, adding that this is the first time a cryptocurrency drain program has targeted mobile users exclusively.
More than 150 users are estimated to have fallen victim to the scam, although it is believed that not all users who downloaded the app were affected by the cryptocurrency leak.
The campaign involved distributing a fraudulent app under several names, such as “Mestox Calculator”, “WalletConnect – DeFi & NFT” and “WalletConnect – Airdrop Wallet” (co.median.android.rxqnqb).
Although the app is no longer available for download from the official app market, data from SensorTower shows that it was popular in Nigeria, Portugal and Ukraine and related to the said developer USA FOX.
The developer was also linked to another Android app called “Uniswap DeFI” (com.lis.uniswapconverter), which remained active on the Play Store for about a month from May to June 2023. It is currently unknown whether the app contained any malicious features.
However, both apps can be downloaded from third-party sources in the app store, which once again highlights the risks associated with downloading APK files from other marketplaces.
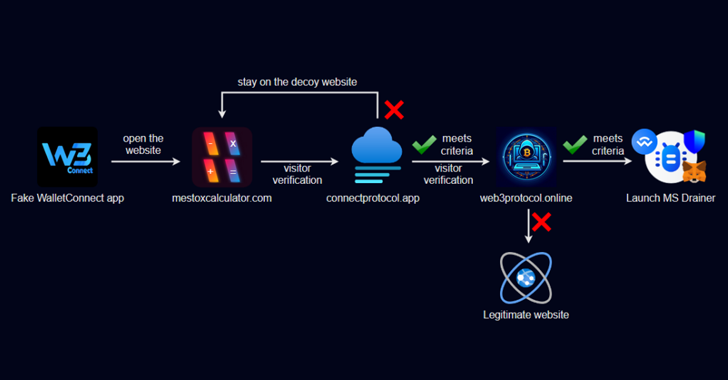
Once installed, the WallConnect spoof is designed to redirect users to a fake website based on their IP address and User-Agent string, and if so, redirects them a second time to another website impersonating Web3Inbox.
Users who do not meet the required criteria, including those visiting the URL from a desktop web browser, are redirected to a legitimate website to avoid detection, effectively allowing threat actors to bypass the Play Store app review process.
In addition to taking measures to prevent analysis and debugging, the main component of the malware is a cryptocurrency drainer, known as MS Drainer, which prompts users to connect their wallet and sign several transactions for the wallet to be verified.
The information entered by the victim at each step is transmitted to the control server (cakeserver(.)online), which in turn sends a response containing instructions to initiate malicious transactions on the device and transfer funds to a wallet address owned by the attackers.
“Similar to stealing one’s own cryptocurrency, the malicious app first tricks the user into signing a transaction in their wallet,” Check Point researchers said.
“With this transaction, the victim authorizes the attacker’s address 0xf721d710e7C27323CC0AeE847bA01147b0fb8dBF (the ‘Address’ field in the configuration) to transfer the maximum amount of the specified asset (if allowed by her smart contract).”
In the next step, tokens from the victim’s wallet are transferred to another wallet (0xfac247a19Cc49dbA87130336d3fd8dc8b6b944e1) controlled by the attacker.

This also means that if the victim does not revoke permission to withdraw tokens from their wallet, attackers can continue to withdraw digital assets as soon as they appear without requiring any further action.
Check Point said it also discovered another malicious app with similar features, “Walletconnect | Web3Inbox” (co.median.android.kaebpq), which was previously available on the Google Play Store in February 2024. It has been downloaded more than 5,000 times.
“This incident highlights the growing sophistication of cybercriminals’ tactics, particularly in the field of decentralized finance, where users often rely on third-party tools and protocols to manage their digital assets,” the company said.
“The malware did not rely on traditional attack vectors such as permissions or keylogging. Instead, it used smart contracts and deep links to silently spend assets when users were tricked into using the app.”