Threat actors have long used typosquatting as a means to trick unsuspecting users into visiting malicious websites or downloading mined software and packages.
These attacks usually involve registering domains or packages with names slightly altered from their legitimate counterparts (eg goog1e.com vs. google.com).
Opponents targeting cross-platform open source repositories rely on developers making typos to get started attacks on software supply chains via PyPI, npm, Maven Central, NuGet, RubyGems, and Crate.
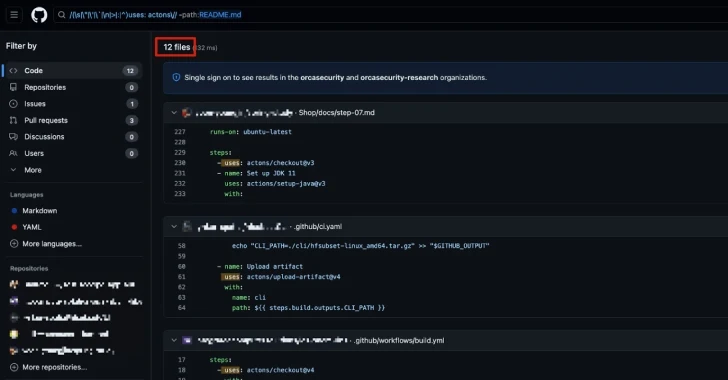
Recent findings from cloud security company Orca show that even GitHub Actionscontinuous integration and continuous delivery (CI/CD) platforms are not immune to the threat.
“If developers make a typo in their GitHub actions that matches the actions of a printing press, it’s possible to cause applications to run malicious code without even realizing it,” security researcher Ofir Jacoby said in a report shared with The Hacker News.
The attack is possible because anyone can publish a GitHub Action by creating a GitHub account with a temporary email account. Given that actions are performed in the context of the user’s repository, the malicious action can be used to forge source code, steal secrets, and use it to deliver malware.
All this method involves is for an attacker to create organizations and repositories with names that closely resemble popular or widely used GitHub activities.
If a user makes an unintentional typo when setting up a GitHub action for their project, and that misspelled version is already created by an adversary, the user’s workflow will take the malicious action instead of the intended one.
“Imagine an action that extracts sensitive information or changes code to introduce subtle bugs or backdoors that could affect all future builds and deployments,” Jacobi said.
“In fact, a compromised action could even use your GitHub credentials to make malicious changes to other repositories in your organization, amplifying the damage across multiple projects.”
Orca said a GitHub search found 198 files that call “action/checkout” or “actons/checkout” instead of “actions/cas” (note the missing “s” and “i”), putting all these projects at risk.
This form of typosquatting is attractive to threat actors because it is a low-cost, high-impact attack that can lead to powerful compromises in the software supply chain, affecting multiple downstream customers at once.

Users are encouraged to double-check actions and their names to ensure they link to the correct GitHub organization, follow actions from trusted sources, and periodically check their CI/CD workflows for typographical issues.
“This experiment highlights how easy it is for attackers to exploit typosquatting in GitHub Actions and the importance of vigilance and best practices in preventing such attacks,” Jacobi said.
“The real issue is even more concerning because here we’re only highlighting what’s happening in public repositories. The impact on private repositories, where the same typos could lead to serious security breaches, remains unknown.”