A new supply chain attack technique targeting the Python Package Index (PyPI) registry has been used in the wild in an attempt to infiltrate downstream organizations.
Codenamed Revival Hijack, JFrog, a software supply chain security company, said the attack method could be used to hijack 22,000 existing PyPI packages and lead to “hundreds of thousands” of malicious package downloads. These sensitive packages have more than 100,000 downloads or have been active for more than six months.
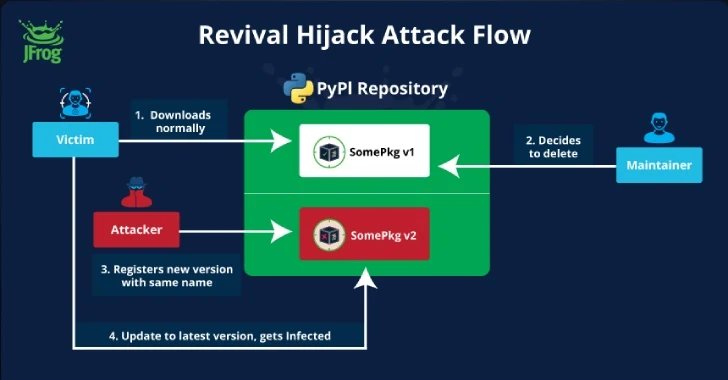
“This attack method involves capturing PyPI software packages by manipulating their ability to be re-registered after they have been removed from the PyPI index by the original owner,” JFrog security researchers Andrei Palkavnichenko and Brian Musali said in the report shared with The Hacker News.
Essentially, the attack involves removing several Python packages published to the PyPI repository, making them available for registration by any other user.
Statistics shared by JFrog show that an average of about 309 packages are removed each month. This can happen for a variety of reasons: lack of maintenance (such as software abandonment), re-publishing a package under a different name, or introducing the same functionality into official libraries or built-in APIs.
It also creates a profitable attack surface that is more effective than typosquatting and that an attacker using their own accounts can use to publish malicious packages with the same name and newer version to infect a development environment.
“The method does not depend on the victim making a mistake when installing the package,” the researchers said, showing how Revival Hijack can perform better from an adversary’s perspective. “Many users consider ‘upgrading a ‘once secure’ package to the latest version to be a safe operation.”
Although PyPI has protections against impersonation and print attempts, JFrog’s analysis found that running “the list of items is outdated” command lists the fake package as a new version of the original package, with the former matching a different package from a completely different author.
More worryingly, the launch of “pip install –upgrade” team replaces the actual package with a fake one without much warning that the package author has changed, potentially exposing unwitting developers to enormous software supply chain risk.
JFrog said he made a new PyPI user account called “security_holding“, which he used to securely capture sensitive packets and replace them with empty placeholders to prevent attackers from exploiting the deleted packets.
Additionally, each of these packages has been assigned a version number of 0.0.0.1 – the opposite of attack of addiction confusion script – to avoid drag and drop by developers when running the pip update command.
More worryingly, Revival Hijack has already been used in the wild, and an unknown threat actor named Ginis is introducing a benign version of the package called “pingdomv3” March 30, 2024, the same day the original owner (Cheneyian) removed the package from PyPI.
On April 12, 2024, a new developer is said to have released an update that contains a Base64-encoded payload that checks for “JENKINS_URL” environment variable and, if present, executes an unknown next-stage module received from the remote server.

“This suggests that the attackers either delayed the attack or designed it to be more targeted, perhaps by limiting it to a specific IP range,” JFrog said.
The new attack is a sign that threat actors are considering supply chain attacks on a broader scale, targeting deleted PyPI packages to expand their reach to companies. Organizations and developers are encouraged to audit their DevOps pipelines to ensure they are not installing packages that have already been removed from the repository.
“Exploiting vulnerable behavior in the handling of remote packages allowed attackers to hijack existing packages, making it possible to install them on target systems without any changes to the user’s workflow,” said Musali, head of JFrog’s security research team.
“The attack surface of PyPI packages is constantly growing. Despite the active intervention, users should always remain vigilant and take the necessary precautions to protect themselves and the PyPI community from this hacking technique.”