Mobile users in Brazil are being targeted by a new malware campaign that is delivering a new Android banking trojan called Rocinante.
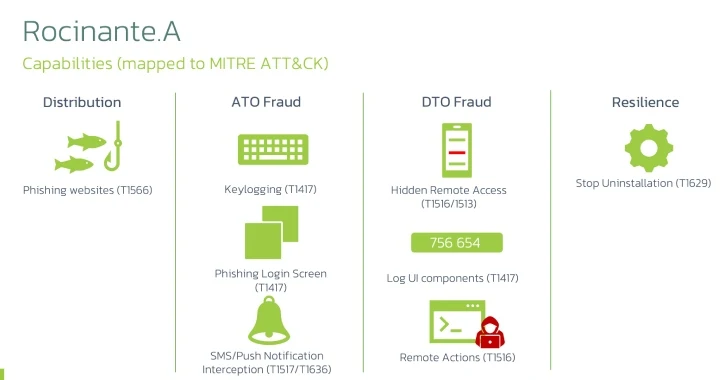
“This malware family is able to perform keylogging using the Accessibility Service and can also steal identifying information from its victims using phishing screens, impersonating various banks,” Dutch security firm ThreatFabric said. said.
“Finally, it can use all of this filtered information to perform Device Control (DTO) by using Accessibility Service privileges to achieve full remote access to the infected device.”
Some of the known malware targets include financial institutions such as Itaú Shop, Santander, with fake programs disguised as Bradesco Prime and Correios Celular, among others –
- Livelo Pontos (com.resgatelivelo.cash)
- Correios Recarga (com.correiosrecarga.android)
- Bratesco Prine (com.resgatelivelo.cash)
- Security Module (com.viberotion1414.app)
Analysis of the source code of the malware revealed that the operators internally call it Rocinante Pegasus (or PegasusSpy). It should be noted that the Pegasus name is not related to the cross-platform spyware developed by commercial surveillance vendor NSO Group.
However, Pegasus is believed to be the work of a threat actor dubbed DukeEugene, who is also known for similar strains of malware such as ERMAC, BlackRock, Hook and Loot. the last analysis by Silent Push.
ThreatFabric said it has identified parts of the Rocinante malware that are directly affected by early iterations of ERMAC, although it is believed that the 2023 leak of the ERMAC source code may have played a role.
“This is the first time that the original malware family took the code from the leak and implemented only a part of it into their own code,” the report notes. “It is also possible that these two versions are separate forks of the same original project.”
Rocinante is primarily distributed through phishing sites that aim to trick unsuspecting users into installing fake dropper programs that, once installed, request Accessibility Service privileges to record all activity on the infected device, intercept SMS messages, and serve phishing login pages.
It also communicates with the command and control server (C2) to wait for further instructions that simulate touch and swipe events to be executed remotely. Collected personal information is transmitted to the Telegram bot.
“The bot extracts useful identifying information obtained through fake login pages that pretend to be targeted banks. It then publishes this information in a chat format that criminals have access to,” ThreatFabric noted.
“The information varies slightly depending on which fake login page was used to obtain it, and includes device information such as phone model and number, CPF number, password or account number.”
The development comes after Symantec singled out another malicious banking trojan campaign that uses the secureserver(.)net domain to target Spanish- and Portuguese-speaking regions.
“The multi-stage attack begins with malicious URLs that lead to an archive containing a garbled .hta file,” the Broadcom-owned company said. said.
“This file leads to a JavaScript payload that performs several AntiVM and AntiAV checks before loading the final AutoIT payload. This payload is uploaded via process injection to steal banking information and credentials from the victim’s system and exfiltrate them to the C2 server. “
It also follows the arrival of a new “extension as a service” being advertised for sale through the new version Genesis Marketwhich was shut down by law enforcement in early 2023 and designed to steal sensitive information from users in the Latin American region (LATAM) using malicious web browser extensions distributed in the Chrome Web Store.

The activity, active since mid-2023 and targeting Mexico and other Latin American countries, has been attributed to a cybercriminal group called Cybercartel, which offers these types of services to other cybercriminal groups. Extensions are no longer available for download.
“A malicious Google Chrome extension disguises itself as a legitimate application, forcing users to install it from compromised websites or from phishing campaigns,” security researchers Ramses Vazquez and Carla Gomez of the Metabase Q Ocelot Threat Intelligence Team. said.
“Once the extension is installed, it injects JavaScript code into the web pages that the user visits. This code can intercept and manipulate page content and capture sensitive data such as login credentials, credit card information, and other user input depending on the specific company and type of information targeted.”