More than 15,000 applications that use the Amazon Web Services (AWS) Application Load Balancer (ALB) for authentication are potentially susceptible to configuration issues that could expose them to access control bypass and compromise applications.
That’s it findings from Israeli cybersecurity company Miggo, which identified the problem ALBeast.
“This vulnerability allows attackers to gain direct access to compromised programs, especially if they are exposed to Internet access,” security researcher Liad Eliyahu said.
ALB is an Amazon service designed to route HTTP and HTTPS traffic to target applications based on the nature of requests. It also allows users to “offload authentication functionality” from their applications to ALB.
“An application load balancer will securely authenticate users when they access cloud applications,” Amazon notes on its website.
“The application load balancer is fully integrated with Amazon Cognito, allowing end users to authenticate through social identity providers such as Google, Facebook, and Amazon, as well as through enterprise identity providers such as Microsoft Active Directory via SAML or any OpenID Connect compliant identity provider. (IdP).”
The attack essentially involves the threat person creating their own instance of ALB with authentication configured in their account.
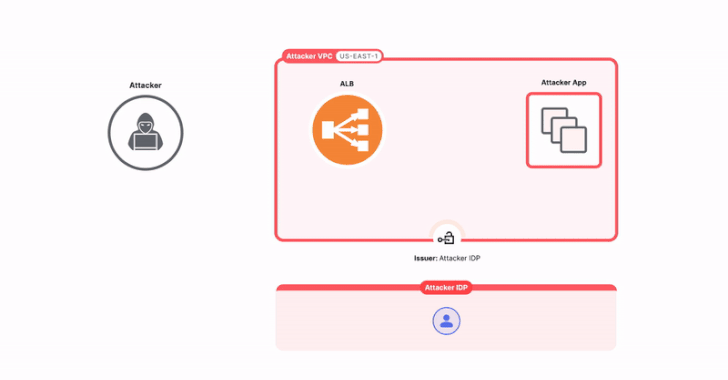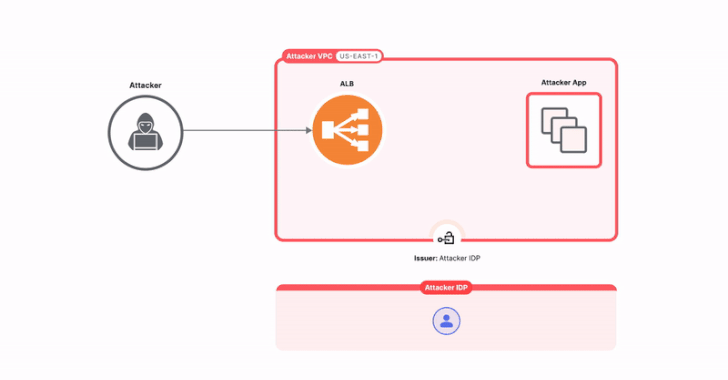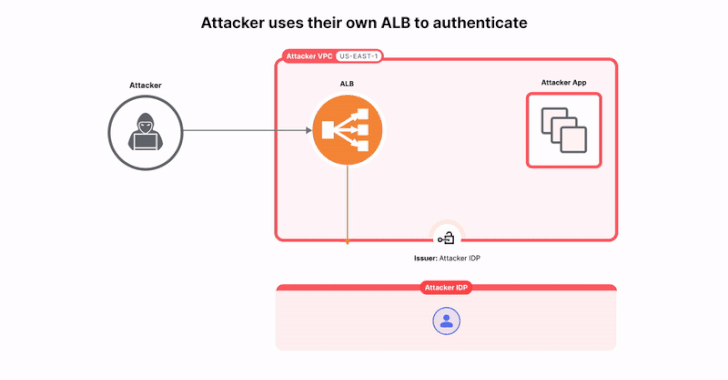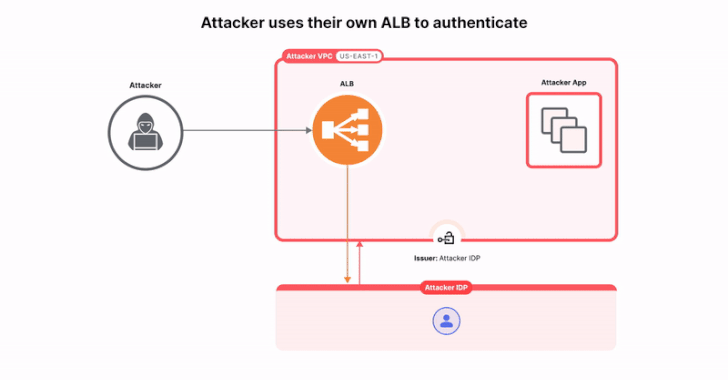
In the next step, ALB is used to sign a token under their control and change the ALB configuration by forging an authentic ALB-signed token with the victim’s identity, ultimately using it to access the target application, bypassing authentication and authorization.
In other words, the idea is for AWS to sign the token as if it actually came from the victim system and use it to access the application, assuming it’s either publicly available or the attacker already has access to it.
After the responsible disclosure in April 2024, Amazon updated the documentation for the authentication features and added new code to verify the subscriber.
“To ensure security, you should verify the signature before performing any claims-based authorization and confirm that the Subscriber field in the JWT header contains the expected Application Load Balancer ARN,” Amazon Now directly states in its documentation.

“Also, as a security best practice, we recommend that you restrict your targets to only receive traffic from your application load balancer. You can achieve this by configuring your targets’ security group to reference the load balancer’s security group ID.’
The discovery comes as Acronis revealed how misconfiguration of Microsoft Exchange can open the door to email spoofing attacks, allowing threat actors to circumvent DKIM, DMARC and SPF protection and send malicious emails impersonating trusted individuals.
“Unless you’ve blocked your Exchange Online organization from only accepting mail from your third-party service, or unless you’ve enabled advanced filtering for connectors, anyone can send you email through ourcompany.protection.outlook.com. or ourcompany.mail.protection.outlook.com and the DMARC check (SPF and DKIM) will be skipped,” the company said in a statement. said.