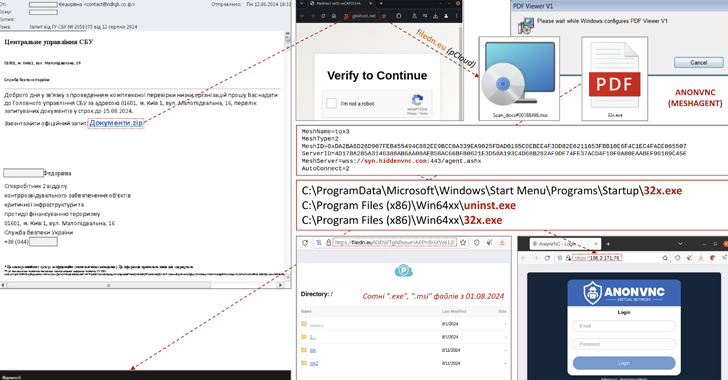
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new phishing campaign masquerading as the Security Service of Ukraine to distribute malware with the ability to remotely access the desktop.
The agency is tracking activity called UAC-0198. It is estimated that since July 2024, more than 100 computers have been infected, including those related to government agencies in the country.
The attack chains involve mass email distribution to deliver a ZIP archive containing an MSI installer file that, when opened, deploys a malware called ANONVNC.
ANONVNC, which is based on an open source remote control tool called MeshAgentallows covert unauthorized access to infected hosts.
The development is delivered as CERT-UA attributed to hacking group UAC-0102 to phishing attacks by distributing HTML attachments impersonating the UKR.NET login page to steal user credentials.
In the past few weeks, the agency has also warned of a surge in distribution campaigns PicassoLoader malware with the ultimate goal of deploying the Cobalt Strike Beacon on compromised systems. The attacks were linked to a threat tracked as UAC-0057.
“It is reasonable to assume that the objects of interest of UAC-0057 can be both design bureau specialists and their “contractors” from among the employees of the relevant local self-government bodies of Ukraine,” CERT-UA notes. said.