Microsoft said it is developing security updates to address two vulnerabilities it says could be used to launch attacks to downgrade the Windows Update architecture and replace current versions of Windows files with older versions.
The vulnerabilities are listed below –
- CVE-2024-38202 (CVSS Score: 7.3) – Windows Update Stack Elevation of Privilege Vulnerability
- CVE-2024-21302 (CVSS Score: 6.7) – Elevation of privilege vulnerability in Windows Secure Kernel Mode
The detection and reporting of flaws belongs to SafeBreach Labs researcher Alon Leviev, who presented the findings on Black Hat USA 2024 and DEF CON 32.
CVE-2024-38202, which is implemented in the Windows Backup component, allows “an attacker with basic user privileges to reintroduce previously mitigated vulnerabilities or bypass certain virtualization-based security (VBS) features,” the tech giant said.
However, it was noted that an attacker attempting to exploit the flaw would need to convince an administrator or user with delegated permissions to perform a system restore that inadvertently causes the vulnerability.
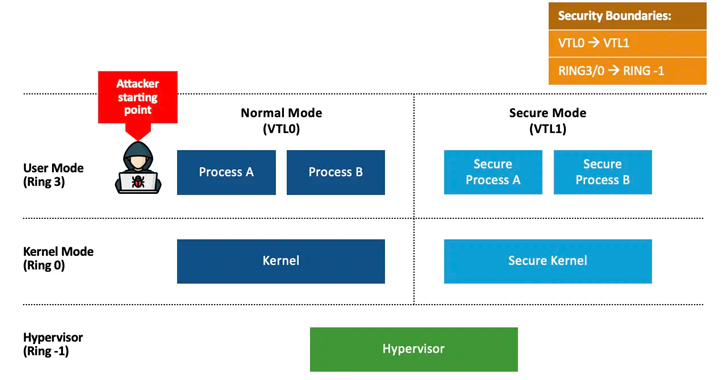
The second vulnerability also addresses the case of elevation of privilege on Windows systems that support VBS, effectively allowing an adversary to replace current versions of Windows system files with outdated versions.
The implications of CVE-2024-21302 are that it can be weaponized to reintroduce previously resolved security flaws, bypass certain VBS features, and leak VBS-protected data.
Leviev, who detailed a tool called Windows Downdate, said this can be used to make “a fully patched Windows machine susceptible to thousands of past vulnerabilities, turning patched vulnerabilities into zero days and rendering the term ‘fully patched’ meaningless on any Windows machine in the world.”
The tool, Leviev added, can “take over the Windows Update process to create completely invisible, invisible, permanent and irreversible downgrades of critical OS components — this allowed me to elevate privileges and bypass security features.”
In addition, Windows Downdate is able to bypass verification steps such as integrity checks and the use of a trusted installer, which actually allows you to downgrade critical operating system components, including dynamic link libraries (DLLs), drivers, and the NT kernel.

On top of that, these issues can be used to downgrade the Credential Guard isolated user mode process, the secure kernel, and the Hyper-V hypervisor to expose past privilege escalation vulnerabilities, as well as disable VBS along with features like hypervisor-protected code integrity ( HVCI).
The end result is that a fully patched Windows system can become susceptible to thousands of past vulnerabilities and turn patched flaws into zero days.
These downgrades have the added effect of telling the operating system that the system is fully up-to-date, while preventing future updates from being installed and preventing detection by recovery and scanning tools.
“The downgrade attack I was able to perform on the Windows virtualization stack was possible due to a design flaw that allowed less privileged virtual layers/rings of trust to update components that reside in more privileged virtual layers/rings of trust,” Leviev said.
“This was very surprising given that the Microsoft VBS features were announced in 2015, which means that the downgrade attack surface I discovered has been around for almost a decade.”