The threat actor associated with North Korea is known as Moonstone continues to push malicious npm packages into the JavaScript package registry to infect Windows systems, highlighting the persistent nature of their campaigns.
The packages in question are harthat-fire and heartthat hash, were published on July 7, 2024, according to Datadog Security Labs. Both libraries did not attract any downloads and were soon discontinued after a short period of time.
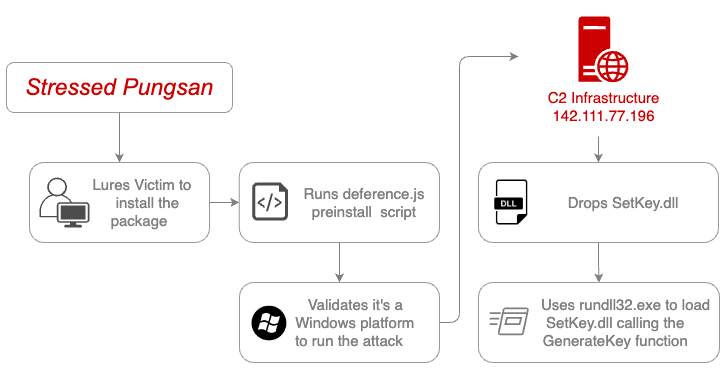
The cloud-monitoring firm’s security unit is tracking a threat called Stressed Pungsan that shows similarities to a recently discovered North Korean malware cluster called Moonstone Sleet.
“While the name reminds today An npm (Ethereum development utility) package, its contents do not indicate an intention to print it.” – Datadog researchers Sebastian Abregaza and Zach Allen said. “The malicious package reuses code from a well-known GitHub repository called node configuration with over 6,000 stars and 500 branches, known in npm as config.”
Attack chains organized by a controversial collective have been known to distribute fake ZIP archives via LinkedIn under a fake company name or on freelancer websites, encouraging potential targets to execute payloads that invoke the npm package as part of a supposed technical skills assessment.
“Once downloaded, the malicious package used curl to connect to an actor-controlled IP address and drop an additional malicious payload, such as SplitLoader,” Microsoft. noted in May 2024 “In another incident, Moonstone Sleet launched a malicious npm loader that led to the theft of credentials from LSASS.”
The following findings are from Checkmarx uncovered that Moonstone Sleet also tried to distribute its packages through the npm registry.
The newly discovered packages are designed to run the pre-installation script specified in the package.json file, which in turn checks to see if it is running on a Windows system (“Windows_NT”), then contacts an external server (“142.111″). .77(.)196”) to load a DLL file that is side-loaded with rundll32.exe binary file.
The malicious DLL, on the other hand, does not perform any malicious activity, indicating either that it was a test run of the payload delivery infrastructure or that it was inadvertently entered into the registry before the malicious code was embedded in it.

The development takes place as South Korea’s National Cyber Security Center (NCSC) warned cyberattacks by North Korean threat groups tracked as Andariel and Kimsuki to deliver malware families such as Dora RAT and TrollAgent (aka Troll Stealer) in intrusion campaigns targeting the construction and engineering sectors in the country.
The series of Dora RAT attacks is notable for the fact that the Andariel hackers exploited vulnerabilities in the internal VPN’s software update mechanism to spread the malware.