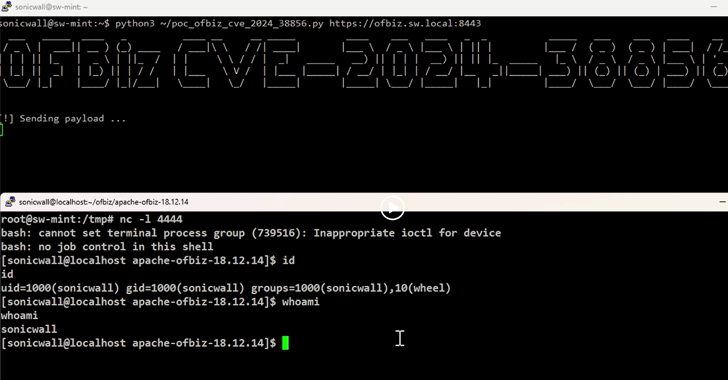
A new zero-day remote code execution pre-authentication vulnerability has been discovered in Apache OFBiz open source enterprise resource planning (ERP) system, which could allow threat actors to achieve remote code execution in affected cases.
Tracked as CVE-2024-38856, the flaw has a CVSS score of 9.8 out of a maximum of 10.0. This affects versions of Apache OFBiz prior to 12/18/15.
“The root cause of the vulnerability is a flaw in the authentication mechanism,” SonicWall, which discovered and reported the flaw, said in a statement.
“This flaw allows an unauthenticated user to access features that would normally require a user to log in, opening the way for remote code execution.”
CVE-2024-38856 is also a patch workaround for CVE-2024-36104path traversal vulnerability that was fixed in early June in the 12/18/14 release.
SonicWall described the flaw as a view override functionality that exposes critical endpoints to unauthenticated threat actors, who can use it to achieve remote code execution via specially crafted requests.
“Unauthenticated access to the ProgramExport endpoint was allowed by associating it with any other endpoints that do not require authentication, abusing the view override feature,” – Security researcher Khasib Vgora said.

This development is another critical path traversal vulnerability in OFBiz that could lead to remote code execution (CVE-2024-32113) has since fallen under active exploitation to deploy the Mirai botnet. It was fixed in May 2024.
Also SonicWall in December 2023 opened a zero-day flaw in the same software (CVE-2023-51467) that allowed authentication protections to be bypassed. It was subsequently subjected to a large number of exploitation attempts.