Cybersecurity researchers have discovered a new Android banking trojan called BlankBot targeting Turkish users to steal financial information.
“BlankBot has a number of malicious capabilities that include client injection, keylogging, screen recording, and communication with a management server via a WebSocket connection,” Intel 471 said in an analysis published last week.
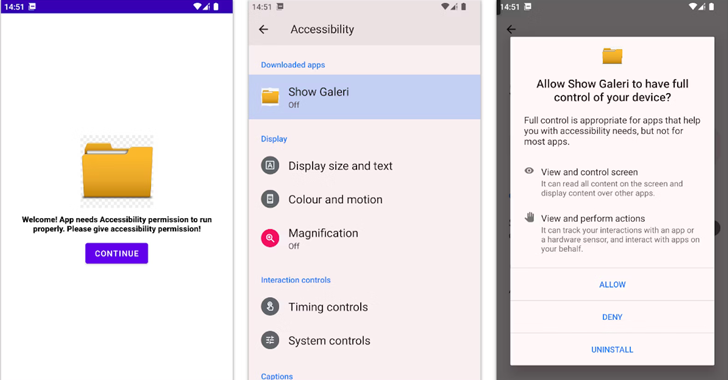
Discovered on July 24, 2024, BlankBot is said to be in active development, with the malware abusing Android Accessibility Services permissions to gain full control over infected devices.

The names of some of the malicious APK files containing BlankBot are listed below –
- app-release.apk (com.abcdefg.w568b)
- app-release.apk (com.abcdef.w568b)
- app-release-signed (14).apk (com.whatsapp.chma14)
- app.apk (com.whatsapp.chma14p)
- app.apk (com.whatsapp.w568bp)
- showcuu.apk (com.whatsapp.w568b)
As recently restored Mandragora An Android Trojan, BlankBot implements a session-based package installer to bypass the Restricted Settings feature introduced in Android 13 to prevent side-loaded apps from requesting unsafe permissions.
“The bot asks the victim to allow the installation of apps from third-party sources, then it extracts an Android Package Kit (APK) file stored in the app’s asset directory without encryption and continues the process of installing the package,” Intel 471 said.
The malware comes with an extensive set of features to perform screen recording, keyboard and overlays based on specific commands received from a remote server to collect bank account credentials, payment data and even the pattern used to unlock the device.
BlankBot is also capable of intercepting SMS messages, uninstalling arbitrary applications and collecting data such as contact lists and installed applications. It also uses the Accessibility Services API to prevent the user from accessing device settings or running antivirus programs.
“BlankBot is a new Android banking trojan that is still under development, as evidenced by the numerous code variants observed in various applications,” the cybersecurity firm said. “Nevertheless, malware can perform malicious actions once it infects an Android device.”
The disclosure comes after Google outlined the various steps it is taking to combat threat actors’ use of cellular site simulators such as Stingrays to inject SMS messages directly into Android phones, a scam known as the SMS Blaster scam.
“This message injection method completely bypasses the operator’s network, thus bypassing all sophisticated network filters to combat spam and fraud,” Google. said. “SMS Blasters Expose a Fake LTE or 5G Network That Does One Function: Downgrade a User’s Connection to the Legacy 2G Protocol.”
Mitigation measures include a user option disable 2G at the modem level and turn off zero ciphersthe latter of which is an important configuration for the false base station to inject the SMS payload.
Earlier in May of this year, Google did too said it enhances cellular security by alerting users when their cellular network connection is unencrypted and when criminals use cellular site simulators to spy on users or send them fraudulent SMS messages.